Securing the DevOps Pipeline Part 2: Hardening Kubernetes and Cloud Security
In Part 2, we shift our focus to securing containerized deployments and cloud infrastructure. We will cover Kubernetes security hardening, real-time monitoring, infrastructure as code (IaC) security, and shifting security left to catch misconfigurations early. These strategies will help your team secure workloads in production and respond to potential threats before they lead to a security breach.





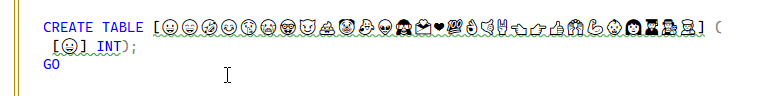 When I check the length, I get these results:
When I check the length, I get these results: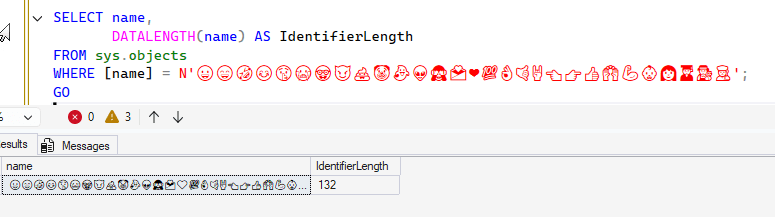 A table name is limited to 128 characters. How does this work?
A table name is limited to 128 characters. How does this work?