Azure Blob Storage Part 9: Shared Access Signatures
In this article, Robin Shahan talks about security and how to control access to containers and blobs using shared access signatures (SAS) and stored access policies.
2015-03-27
7,596 reads
In this article, Robin Shahan talks about security and how to control access to containers and blobs using shared access signatures (SAS) and stored access policies.
2015-03-27
7,596 reads
'Temporal' tables contain facts that are valid for a period of time. When they are used for financial information they have to be very well constrained to prevent errors getting in and causing incorrect reporting. This makes them more difficult to maintain. Is it possible to have both the stringent constraints and simple CRUD operations? Well, yes. Dwain Camps patiently explains the whole process.
2015-03-26
9,819 reads
As big data application success stories (and failures) have appeared in the news and technical publications, several myths have emerged about big data. This article explores a few of the more significant myths, and how they may negatively affect your own big data implementation.
2015-03-25
11,670 reads
In order to automate the delivery of an application together with its database, you probably just need the extra database tools that allow you to continue with your current source control system and release management system by integrating the database into it. If you're using the Microsoft stack, then Redgate's tools can help with some of the difficult database parts of the process, as Jason Crease demonstrates.
2015-03-24
8,081 reads
What are the SQL Server Reporting Services Document Map and Bookmark properties? How can they be used? Do they work for all rendering formats? Scott Murry answers these questions and more.
2015-03-23
8,334 reads
In this article, Robin Shahan explains what Blob Leases are and how to use them, including code samples for calling the different methods available for managing Blob Leases.
2015-03-20
7,310 reads
Database Design is one of those tasks where you have to carefully get all the major aspects right. If you mess-up just one of these, it can all go horribly wrong. So what are these aspects that can ruin database design, and how can you get them right? Robert Sheldon explains.
2015-03-19
17,062 reads
Greg Larsen discusses the ROLLUP, CUBE and GROUPING SETS operators. These operators are used with the GROUP BY clause and allow you to create subtotals, grand totals and superset of subtotals. Read on to find out more about these additional GROUP BY operators.
2015-03-18
11,340 reads
Behaviour Driven Development (BDD) is not always clearly understood, and the term is particularly unfamiliar in database circles. Seb Rose introduces us to the fundamentals of BDD, and make some suggestions for how it might be relevant to database development.
2015-03-17
8,807 reads
Next to the average and the median, there is another statistical value that you can calculate over a set: the mode. This is the value that appears the most often in the set. The average and the median are straight forward to calculate with T-SQL in SQL Server, but how can we determine the mode using T-SQL?
2015-03-16
6,205 reads
By Steve Jones
AI is a big deal in 2026, and at Redgate, we’re experimenting with how...
By Steve Jones
Another of our values: The facing page has this quote: “We admire people who...
By Ed Elliott
Running tSQLt unit tests is great from Visual Studio but my development workflow...
Comments posted to this topic are about the item No Defaults Passwords Ever
Hi, We have low latency high volume system. I have a table having 3...
Comments posted to this topic are about the item The Long Name
I run this code to create a table: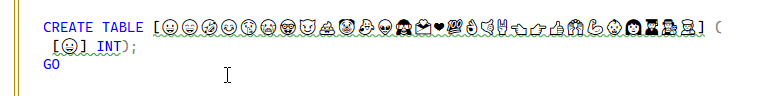 When I check the length, I get these results:
When I check the length, I get these results: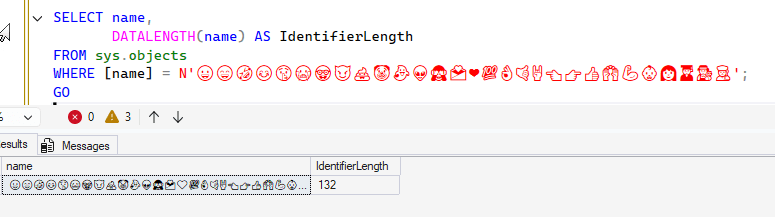 A table name is limited to 128 characters. How does this work?
A table name is limited to 128 characters. How does this work?