Review of AppRadar™
![]()
Introduction
Are you working in a large enterprise where your databases are of extreme value and security of that data is the utmost of importance? Are you looking for a real-time, active Microsoft SQL Server™ database intrusion protection system (Db-IPS) that directly monitors databases for malicious activity and provides "database-specific" protection and monitoring? Well, then, AppRadar™ is possibly for you!
AppRadar™ provides detection/prevention at the application layer (not just the transport/network layers), whether the attack is from a valid user or intruder, and provides a reliable method of monitoring and preventing attacks for enterprise databases even if the attack is embedded deeply within a SQL command. The "intelligent database security sensor" works alongside existing operating system and network operating system security sensors. AppRadar™ also facilitates information security lockdown policies to ensure more efficient use of enterprise IT resources, and it provides a centralized management of database audit events on attack information that empowers organizations to manage large amounts of database attack, audit, and system events. AppRadar™ is host-based and can send alerts to either your existing monitoring infrastructure or to Application Security, Inc.'s own Enterprise Management Console. AppRadar™ meets Common Vulnerabilities and Exposures (CVE) requirements (http://www.cve.mitre.org/compatible/organizations.html#appsecinc), and it provides a continuously updated database security knowledge base via ASAP updates which are backed by Application Security, Inc.'s own research and development team (SHATTER).
AppRadar™ consists of seven elements:
- AppSecInc Console: A web-based application accessible via a web browser. Installed on a shared, network-accessible host that configures/monitors AppRadar™ Sensor activity. Events (configuration and security alert data) reported by the Sensors are archived or saved for presentation via the Console. A single AppSecInc Console can monitor thousands of databases (scalable architecture).
- AppRadar™ Sensor: Installed on each database that AppRadar™ will
monitor and protect. The lightweight, real-time Sensor hooks directly into the database and monitors
activity for malicious behavior which is recorded, processed, and
forwarded to the AppRadar™ Console.
- AppRadar™ Alerts: Alerts/notifications are sent out when a Sensor detects a database event. Delivered through a number of different methods (i.e. E-mail, SNMP, log files, Third-Party Management Consoles, AppSecInc Console, etc.).
- Policies: A collection of rules that dictates what the Agent should monitor. Users can use built-in policies created by Application Security during installation or create policies manually. Policy management is done via the AppSecInc Console. Changes are deployed to the Agents via an SSL connection.
- Rules and Rule Categories:
- Accessing Operating System Resources: Rules that enable organizations to monitor attackers trying to gain access to the host operating system through Microsoft SQL Server.
- Auditing Information: Rules in this category provide an easy way to audit databases and track what data has been accessed, highlighting any changes to permissions within the database -- all without impacting system performance or modifying applications.
- Buffer Overflow Attacks: Rules in this category can be enabled to send an alert any time an attacker is taking advantage of all the existing buffer overflow vulnerabilities in Microsoft SQL Server. Buffer overflow vulnerabilities allow attackers to overwrite the stack and execute code under the security context of Microsoft SQL Server.
- Password Attacks: Rules in this category monitor the use of password-related attacks such as when an attacker is repeatedly attempting to log into a database using different account and password combinations either manually or automatically through scripts.
- Privilege Escalation: Rules in this category that monitor for individuals attempting to elevate their privileges to gain enhanced access to the database.
- Web Application Attacks: Rules within this category can be enabled to monitor against possible access-related attacks. Attacks comprising of this like when an attacker attempts to elevate his or her privileges and gain access to powerful resources within a Microsoft SQL Server database. SQL Injection attack rules can also be set within this category. SQL Injection is when an attacker is “injecting” or manipulating SQL code. It is through adding unexpected SQL to a query that an attacker is able to manipulate a database in many unanticipated ways.
- System Events: Rules within this category can be enabled to send an alerts on events affecting status and integrity of the AppRadar™ Sensor.
- Exceptions: Act as a filter for policy rules. Instead of turning off a particular rule, users can choose to configure an exception that stops the firing of an alert if certain conditions occur. For example, if you configured AppRadar to check for rule "Database Stopped" on a particular database's Agent, you might want to create an exception if the database user is "sa". Then if that database is stopped, the Agent will only fire the alert if the database user is not "sa" since it does not satisfy the exception.
- Auditing: A feature that allows you to specify your audit policy rules in much greater detail. For example, you may wish only to monitor SQL SELECT statements that execute against the customers table in the Northwind database. AppRadar allows you to define a "SELECT from User Table" audit for that table. Once the audit is deployed to the Agent, AppRadar will only fire alerts for the "SELECT from User Table" rule if a SQL SELECT statement is executed against that specific database table.
The AppRadar™ Structure is shown as follows (Figure 1):
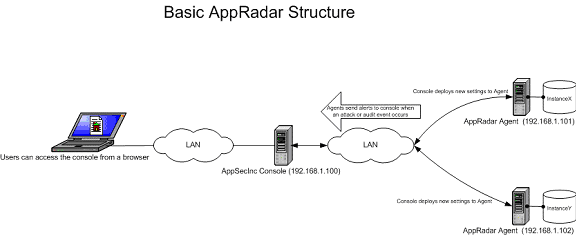
Figure 1
Note: It is okay to install the Console and the Agent on the same server as long as you want to monitor the SQL Server instance that is on the Console machine (make sure the ports you configured for the Console and the Agent are both open).
Simple Object Access Protocol (SOAP) over Hyper Text Transfer Protocol (HTTP) is the communication protocol used between the Console and the Agent. SOAP is executed over a secure sockets layer (SSL) channel. Certificate requests are generated by the Console and the Agent, each of which are generated on the respective host machines. These certificates are signed by a certificate authority (CA) root certificate generated by the Console during installation. The Console's certificate request is signed during the Console's installation. The Agent's certificate request is signed during Agent registration. The Agent receives requests from the Console via its SSL SOAP connection on a port and the Console receives notifications from the Agent via its SSL SOAP connection on a port.
Installation
The installation process requires two installers:
- AppSecInc Console - Web-based application used to manage and receive alerts from the AppRadar Agents. Install the AppSecInc Console on a machine that is connected to the network continuously if you want to receive alerts sent by the Agent around the clock. For strictly managing AppRadar Agents, you can install on an administrator's workstation that is not running constantly..
- AppRadar Agent - Install on the machine where the database server is resident.
Both installations require that you are logged on as a user that belongs to the Windows Administrators group.
The AppSecInc Console installation is very easy and basically consists of a welcome screen, license agreement, port configuration screen (you can change it from default if necessary), and Java™ 2 Runtime Environment installation (if needed). The installation process creates nine Microsoft Windows groups with the following permissions:
- AppSecIncAdmins - Full control of the AppSecInc Console for the Console.
- AppSecIncViewers - Ability to look at all data in both AppDetective and AppRadar.
- AppSecIncUsers - Ability to connect to the AppSecInc Console for both AppRadar and AppDetective.
- AppRadarAdmins - Full control of AppRadar for the Console.
- AppRadarViewers - Ability to look at all data in AppRadar.
- AppRadarUsers - Ability to connect to AppRadar portion of AppSecInc Console.
- AppDetectiveAdmins - Full control of AppDetective for the Console.
- AppDetectiveViewers - Ability to look at all data in AppDetective.
- AppDetectiveUsers - Ability to connect to AppSecInc Console for AppDetective.
Upon completion of the installation, you will be asked if you want to launch the AppSecInc Console. If you don't want to launch it at that time, you can access it by starting your Web browser and connecting to https://YourMachineName:InstallPort (i.e. https://localhost:20080).
The AppRadar Agent installation consists of a welcome screen, license agreement, port configuration (you can change it from default if necessary), and selection of which Microsoft SQL Server 2000 instance to be monitored. To configure more than one instance, run the installation again for each instance. The "AppRadar Agent for InstanceName" (i.e. AppRadar Agent for $TESTSQLSERVER) will be used to run the service as well as log into the database. It is granted the sysadmin role in the SQL Server instance and is created with the privilege of "Log on as a Service" only. A random cryptographic password is created that should not have to be reset.
Environment
AppSecInc Console System Requirements:
- Operating System: Windows 2000 / Windows XP / Windows Server 2003
- Browser: Internet Explorer 4.01 Service Pack 2 or Higher
- Privileges on the Machine: Administrative Privileges are Required to Install the Console
- Network Connectivity: Must exist between the Console and the Sensor
- Hard Drive: 100 MB of Free Disk Space. Additional space may be required depending on the
amount of monitoring data collected
AppRadar™ Sensor Resident on Database:
- Database: Microsoft SQL Server 2000 or MSDE 2000
- Operating System: Windows NT 4.0 Service Pack 5 or Later / Windows 2000 / Windows XP
Professional with Service Pack 1 / Windows Server 2003
- Hard Drive : 10 MB of Free Disk Space
- Privileges: Administrative Access to Microsoft SQL Server
- Network Connectivity is Required
Using AppRadar™
You can Start and Stop the AppSecInc Console and/or the AppRadar Agent service (both set to start up automatically by default) either through the Microsoft Services snap-in or you can do it through the command prompt (C:\>net stop "AppSecInc Console", C:\>net start "AppSecInc Console", C:\>net stop "AppSecInc AppRadar Agent for $MSSQL$INSTANCENAME", C:\>net start "AppSecInc AppRadar Agent for $MSSQL$INSTANCENAME").
The AppSecInc Console authentication is implemented using a module that is designed to work
with a number of existing user directories. Currently, the authentication module works with
Windows NTLM and Active Directory. Future versions will provide support for LDAP and other
user directories. Administrators can add users to an AppSecInc Console group by placing that user's Microsoft
Windows account in the Microsoft Windows local group on the server.
When you launch the browser and access the Console Web page (which utilizes Secure Sockets Layer communication), you will be asked to log in with your fully-qualified name of the Windows account (see Figure 3):
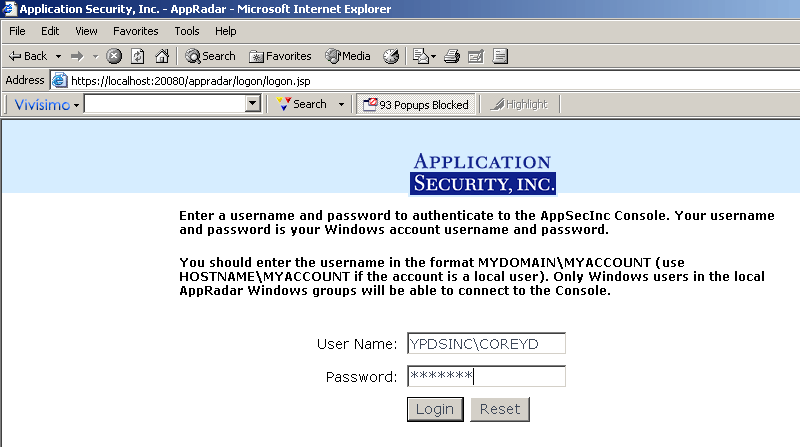
Figure 2
The home page of the console appears as follows (see Figure 3):
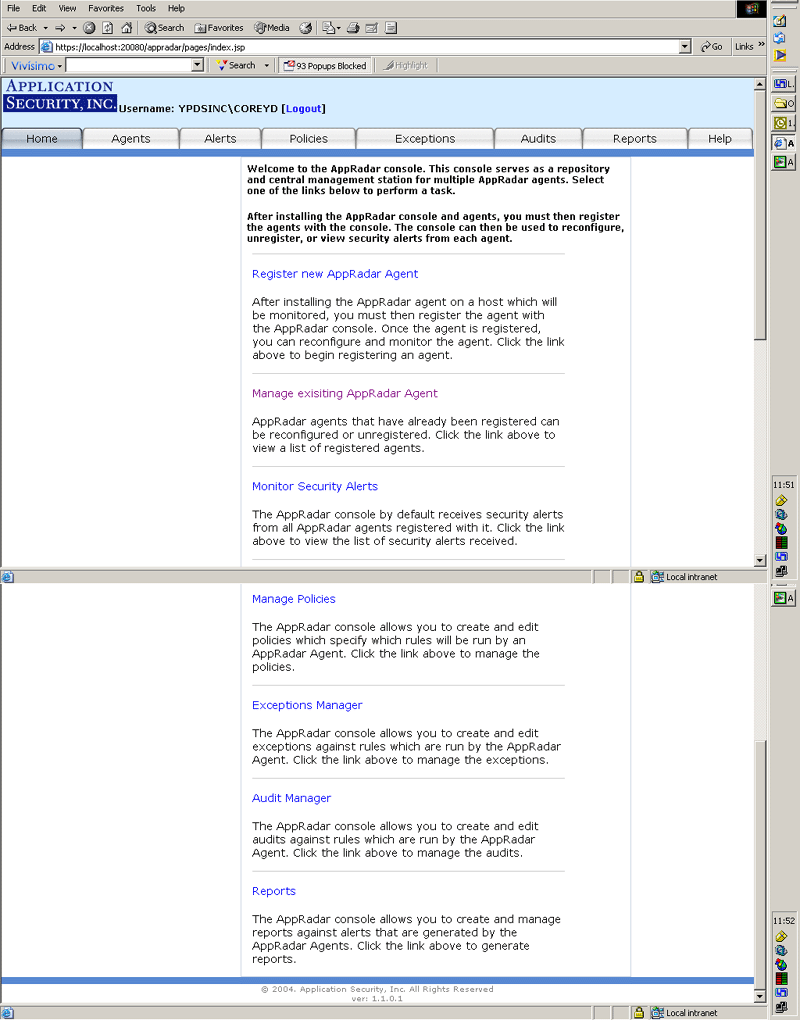
Figure 3
You will need to register each AppRadar Agent you installed (see Figure 4) by clicking on Register New AppRadar Agent link (shown above in Figure 3).
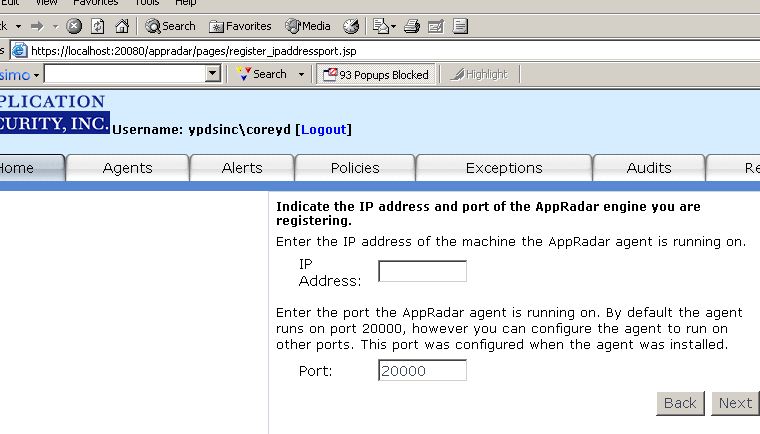
Figure 4
You will then be asked where you want the alert sent (Figure 5). AppConsole is greyed out because, by default, all Registered Agents must send alerts to AppSecInc Console (non-configurable). If you checked the "File" option, alerts will be written to a file named
appradar_notifications.txt in your appradar_install_directory/logs directory.
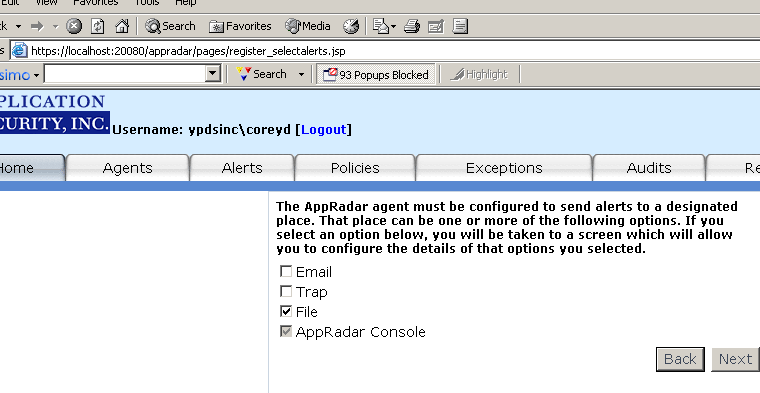
Figure 5
Next, you will be asked what policies you want to enforce, either built-in or created (Figure 6). Different environments require different policies, since what may be malicious for one
database server may be standard behavior for another. You can review the policies by clicking on
the policy name. See the Introduction section for rule categories. Note: You can only choose from one of these policies.
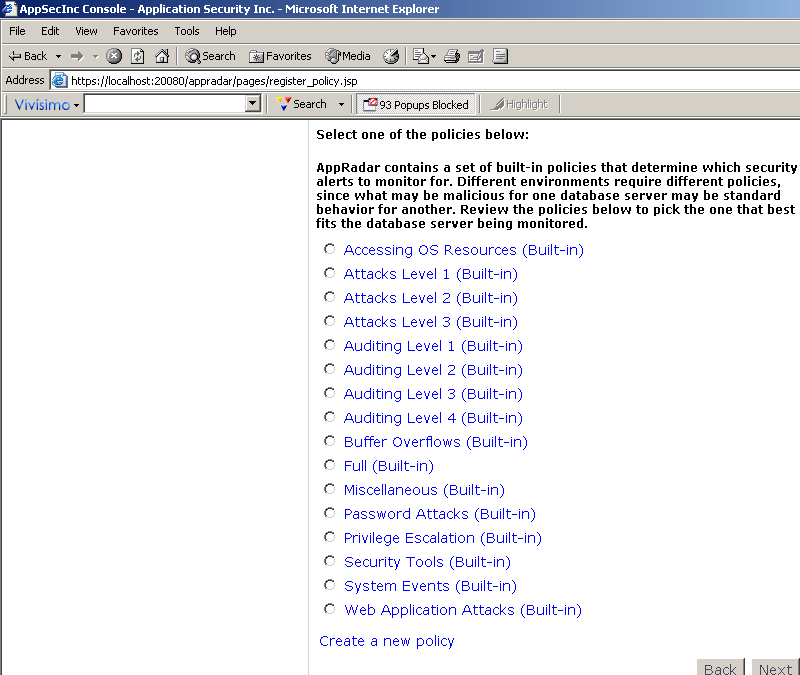
Figure 6
For instance, see Figure 7 below for the options that would be selected if you chose the Attack Level 1 (Built-in) policy .
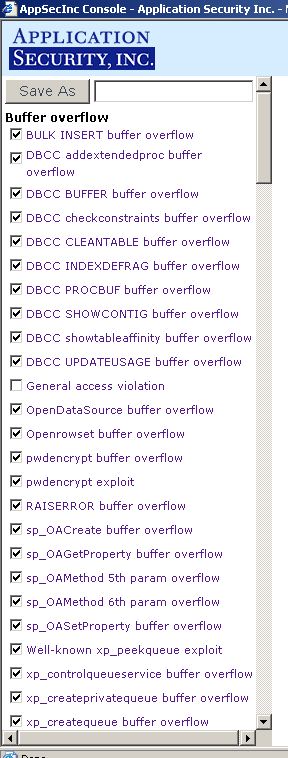 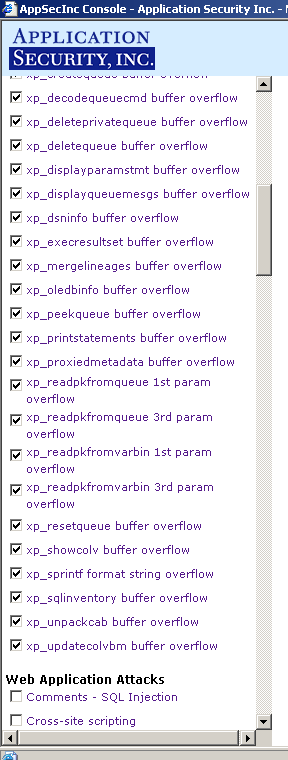 | 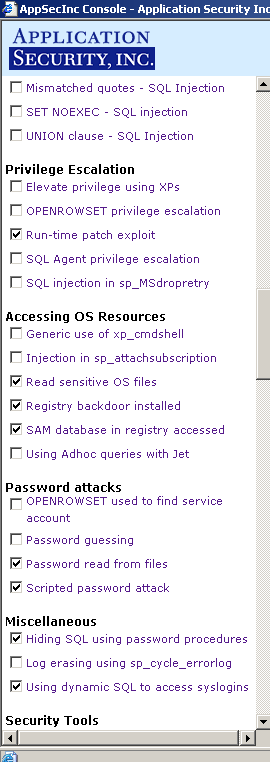 | |
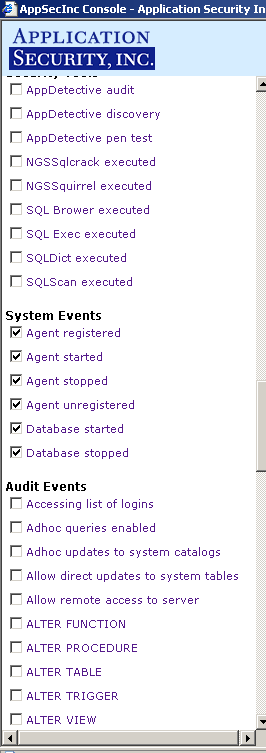 |  |  |
 | ||
Figure 7
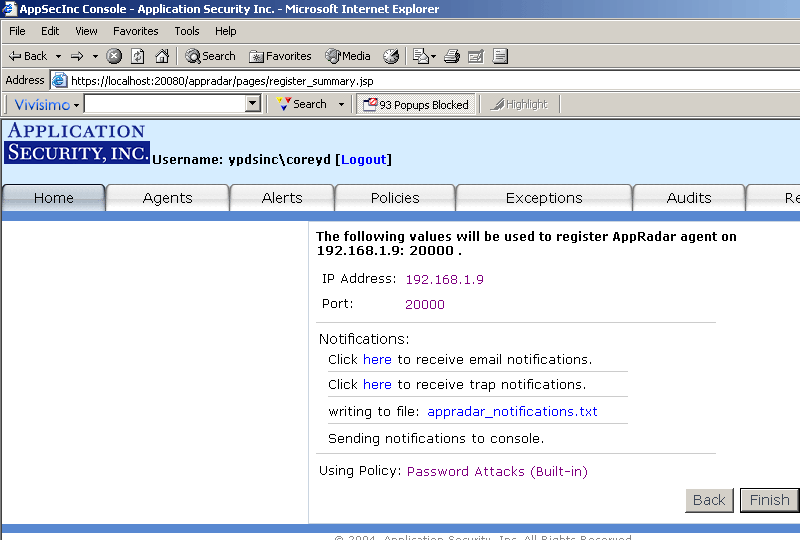
Once you click on the Finish button, you will see the following screens to confirm the agent has been registered (Figure 8):
 |
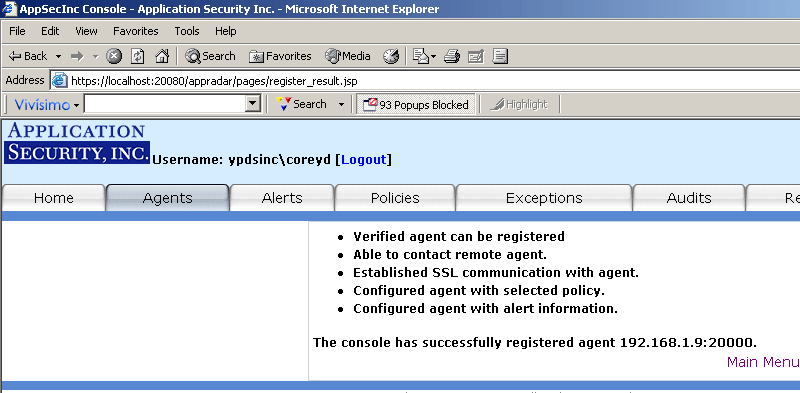 |
Figure 8
Once you create an Agent, you can always edit it as well as unregister the Agent by clicking on the Agents tab (Figure 9).
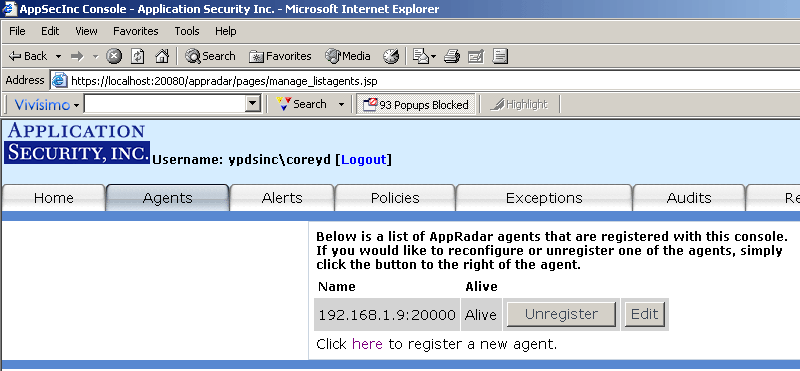
Figure 9
Attention! If you Edit an Agent, it will not take effect until you click on Policies and Deploy it! If you don't Deploy it, the Alerts page will still contain the alerts for your old policy.
NOTE from AppRadar: The policy will take effect once the agent is deployed. New alerts will appear in Alerts page based on the new policy (old alerts will remain).
Figure 10 illustrates the AppRadar notification structure.
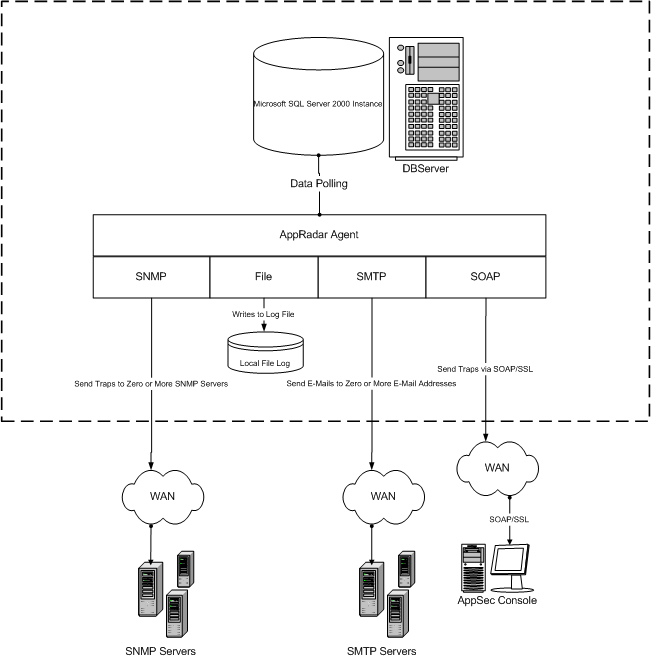
Figure 10
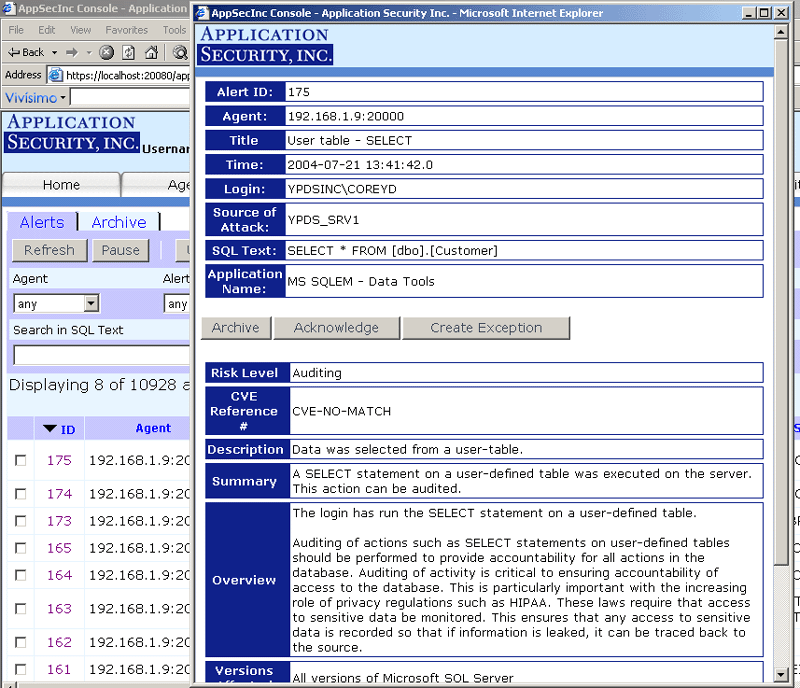
Figure 11 illustrates the Monitor Security Alerts page for viewing security alerts.
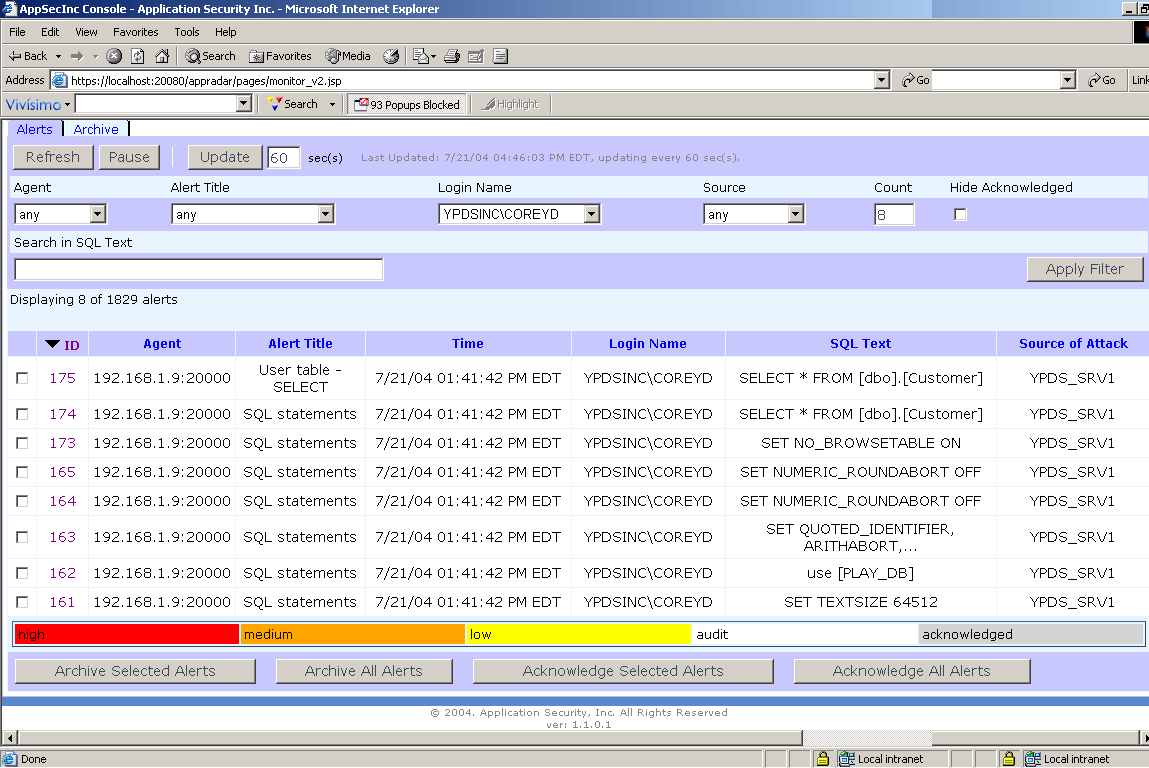
Figure 11
The AppSecInc Console for monitoring security alerts provides the following features:
- Sorting - Sort all the alerts by a certain category.
- Acknowledgement - Acknowledge that you have read the alerts.
- Archive - Archive alerts and then view them by clicking on the "Archive" tab
at the top.
- Filtering - Allows you to selectively choose what you want to see. For
example, if you want to see all the alerts with SQL text "Select", just type "Select" in the
"Search in SQL Text" field, and click "Apply Filter". You can also filter out alerts from specific Agents, particular
alert titles, individual login names, or originating from a known source. In addition, you
can increase the alert count you can view, and hide alerts that you have acknowledged.
- Refresh - Choose to refresh the alerts page every X number of seconds.
- Delete - In order to completely remove an alert, you must first archive it. Then, you can delete it.
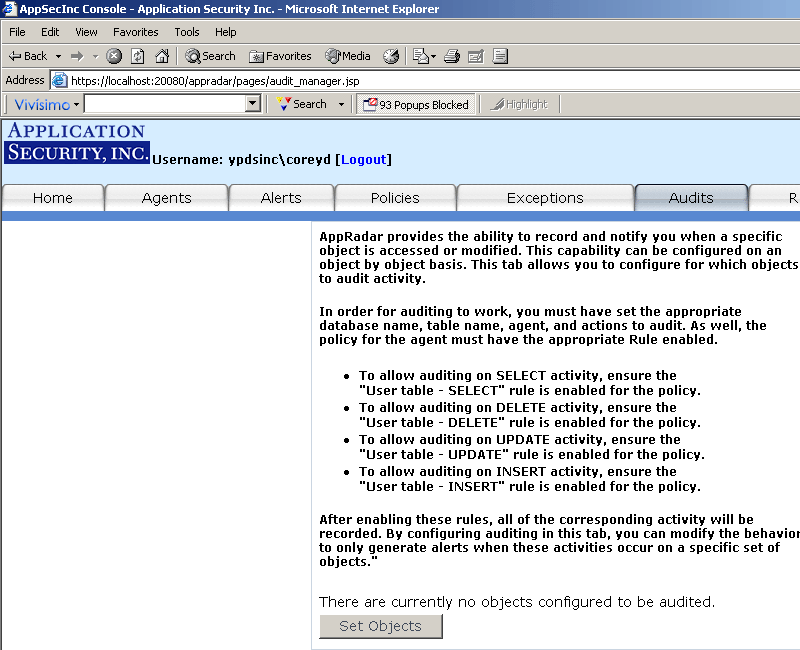
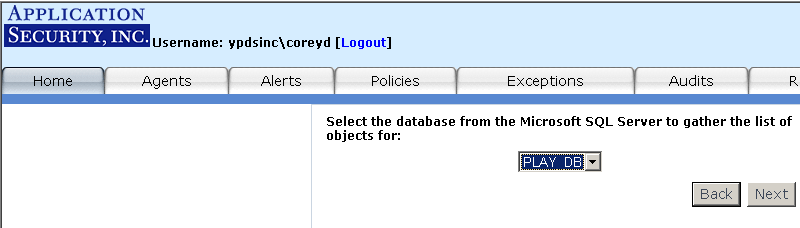
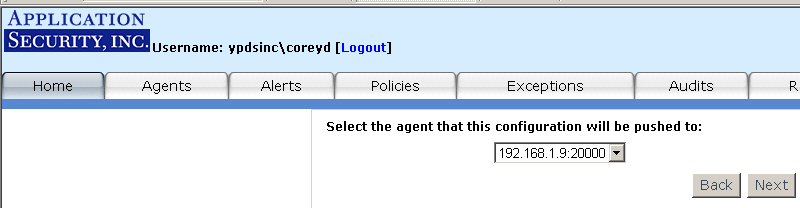
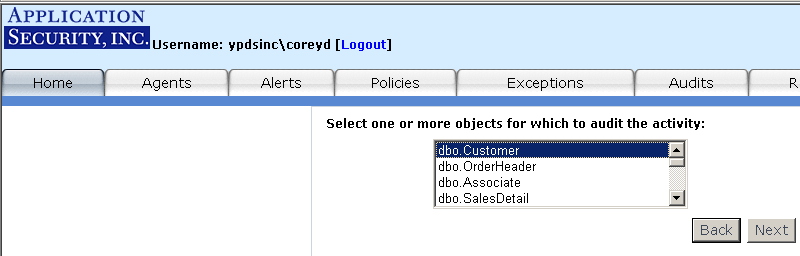
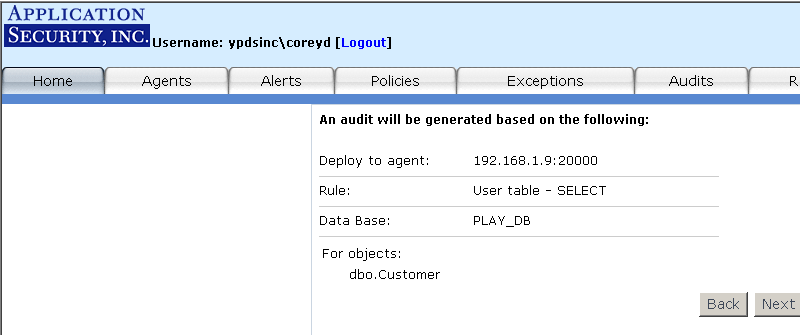
Use the auditing feature to specify your audit policy rules. For example, you
may wish to only monitor those SQL SELECT statements that executed against the "customers"
table in the "Northwind" database. You may define a "SELECT from User Table" audit for that
table. Once the audit is deployed to the Agent, AppRadar will only fire alerts for the "SELECT
from User Table" rule if a SQL SELECT statement executes against that specific database table.
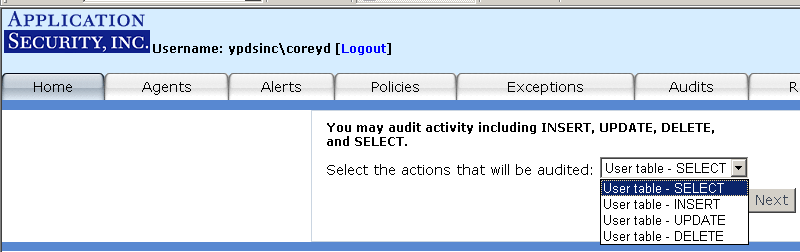
To access the auditing feature, click on the "Audits" tab or on the "Audit Manager" link from the
main page (see Figure 12).
 |
 |
 |
 |
 |
 |
 |
Figure 12
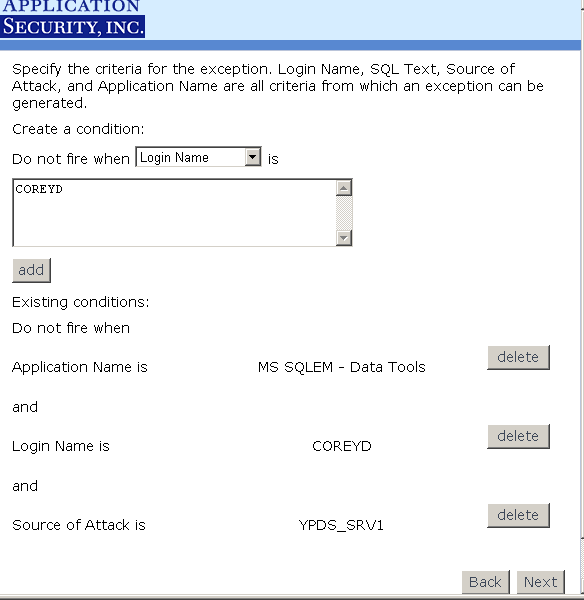
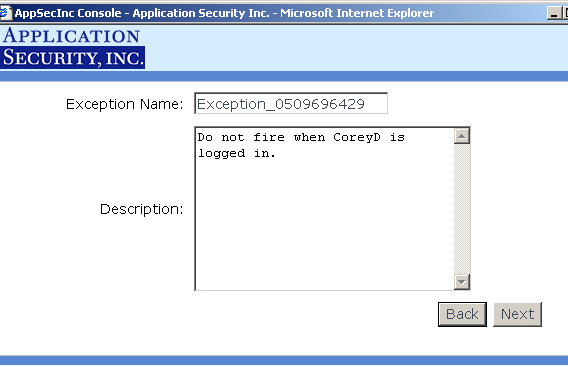
You can add exceptions which are ways to specify temporary conditions that, when met, preclude an alert from
firing. You can do so either from the Monitor Alerts page which is the recommended approach (see Figure 13) or Manage Exceptions page. After you create an exception for a particular Agent, you may want to edit that exception and re-deploy
it to the Agent. On the Manage Exceptions page (see Figure 14), next to the Agent name there is a button
labeled "Redeploy" (if you already have an exception created). If you click on that button, you
will redeploy all exceptions related to that Agent.
 |
 |
 |
 |
 |
 |
Figure 13
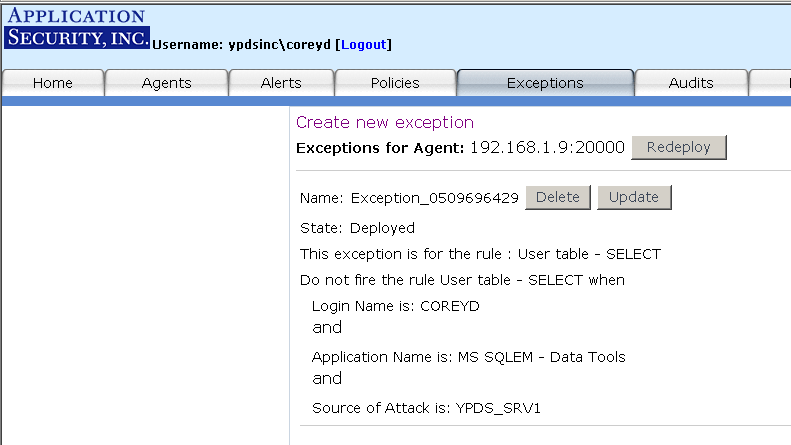
Figure 14
Note: To create exceptions for multiple users, you will need to create a new exception for each user.
To generate a new report from the "Reports" page,
click on the "Create New Report" button to start the Report wizard.
The wizard will guide you through the following steps (see Figure 15 for screen shots):
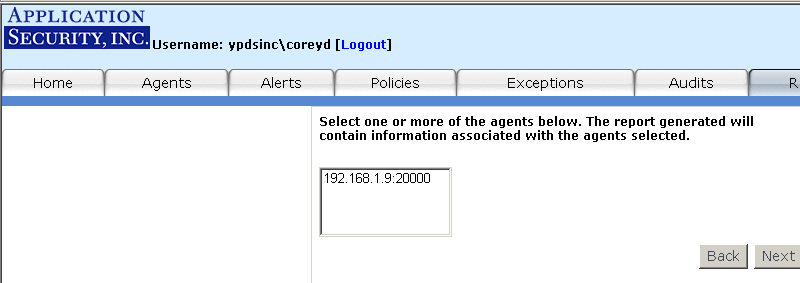
Step 1: Select an Agent - The first step is to
select the Agent(s) that the alerts to be included come from. If you wish to
select more than one Agent, hold down the "Ctrl" key and left click
on multiple Agents to select them. Click "Next" to continue.
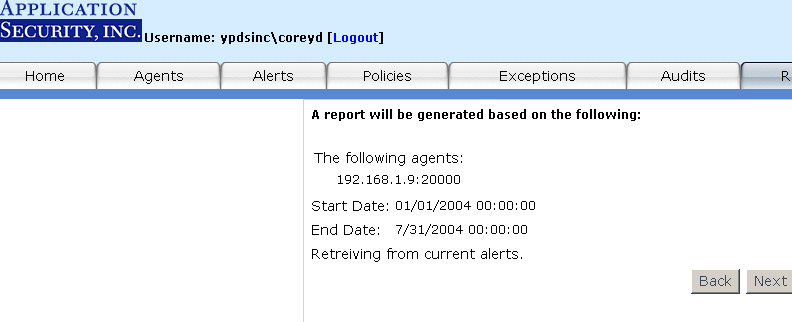
Step 2: Input a
Date Range - The next step is to enter a report date and time range. The report
generated will be based on the date and time specified. The format should be in
"MM/DD/YYYY-HH:MM:SS". You can cut and paste the time format based on
the time field in the Alert Manager.
Step 3: Select
the Location of the Alerts - Select whether the alerts are located in the
"Alerts" tab or "Archive" tab in the Alerts Manager.
Step 4: Confirm
Settings - Review the summary page and make sure the settings are correct. Click
"Next" to generate the report.
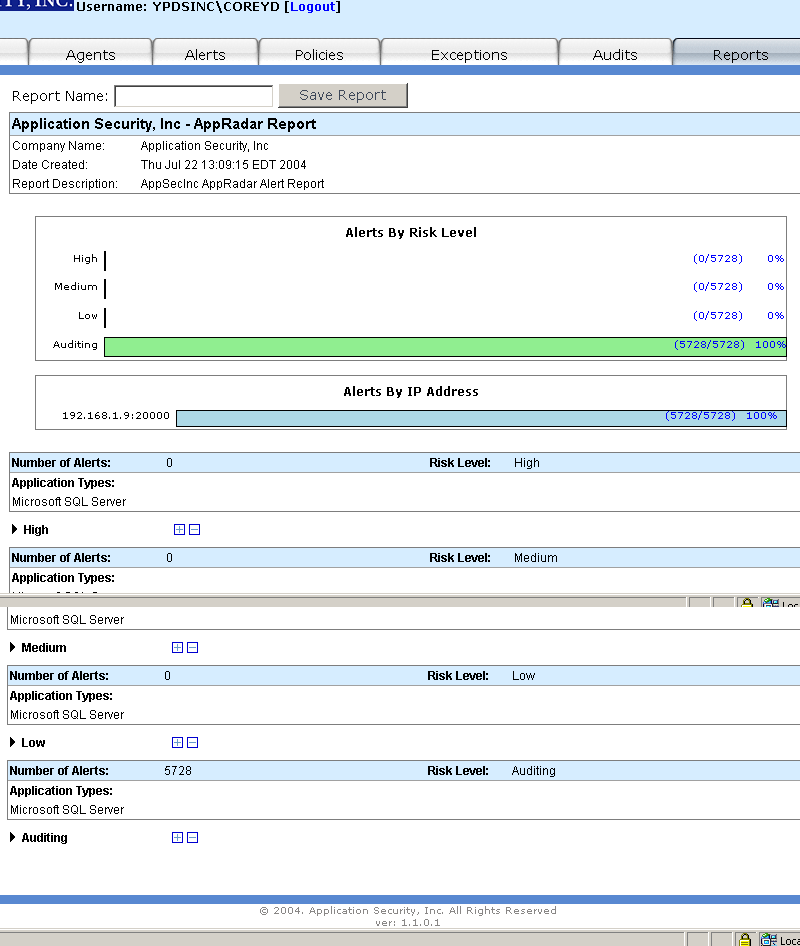
Step 5: Report
Successfully Created - You have successfully created a report. You can now review
or print its contents or save it for later review.
 |
 |
 |
 |
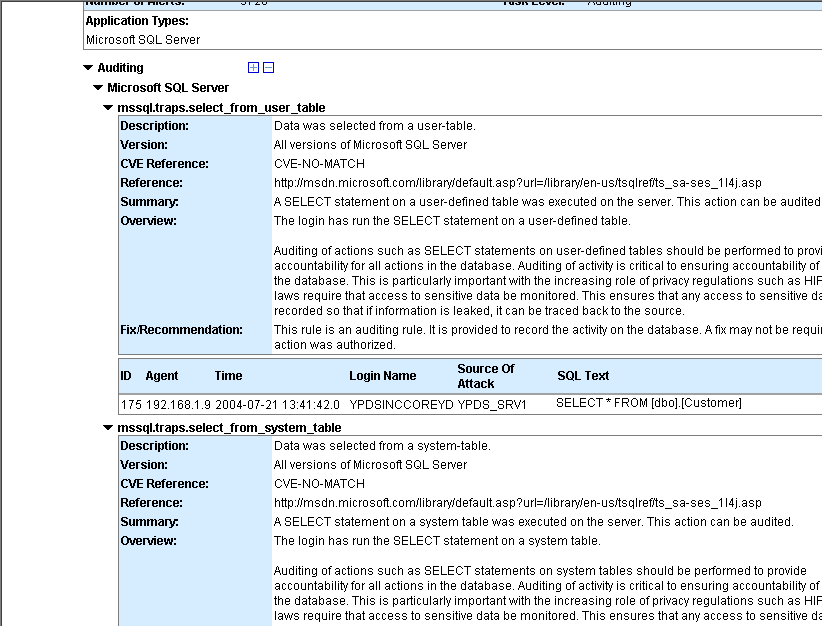 |
Figure 15
Other Things to Know about AppRadar™
Q1. Is AppRadar™ dependent on Microsoft SQL Server Auditing?
A1. No, AppRadar™ operates independently of Microsoft SQL Server Auditing. Using Auditing Information rules, AppRadar™ provides audit trails of database activity offering easy insight into users and applications. For example, with these rules users can audit databases, tracking data access and permission changes without degrading system performance or modifying applications.
Q2. How is AppRadar™ an effective and low impact auditing solution for Microsoft SQL Server?
A2. Regulatory requirements mandate that organizations continuously monitor and audit their databases, identifying any intrusive activities that might compromise critical financial information. AppRadar™'s auditing capabilities for Microsoft SQL Server empower organizations to capture all DML, DDL, Audit, and Security statements happening. Furthermore, AppRadar™ monitors SELECT, INSERT, UPDATE, DELETE, CREATE, ALTER, and DROP statements, as well as security changes at the LOGIN and USER level.
Q3. Doesn't Microsoft SQL Server already have auditing features that satisfy existing regulatory requirements?
A3. Although Microsoft SQL Server includes auditing features like C2 Compliance and SQL Trace, these features lack intelligence and may require significant effort to configure correctly. Moreover, they lack built-in logic to detect malicious activity. All activity is simply logged and written to a local file or table which fails to provide adequate security. Because the data is stored locally, anyone that can audit or monitor the database can access and change the audit trail logs. Thus, an attacker that breaks into the system, will also have access to these logs and will likely eliminate the audit trail, or just delete individual records, to hide their footprints. Similarly, a database administrator that wants to perform illegal actions will simply remove any record of the malicious activity from the local audit logs.
Q4. Can AppRadar™ define exceptions or filters against audit rules or attack signatures?
A4. AppRadar™'s “exceptions” engine acts as a filter for policy rules. Instead of turning off a particular rule, users can set an exception so that alerts will not fire under specified conditions. For example, if AppRadar™ checks for “Database Stopped” on a particular Sensor, you might want to create an exception for when the database user is an administrator. Then, if the database is stopped, the Sensor will only fire an alert if the database user is not an administrator.
Q5. How does AppRadar™ respond to attacks?
A5. Upon detection of an attack, unauthorized activity, or other specified event, AppRadar™ can respond in one or more of the following manners:
E-mail – Each AppRadar™ Database Sensor can send notifications via electronic mail when an AppRadar™ Alert is fired.
SNMP Consoles – AppRadar™ can forward SNMP traps to any server that can accept them.
- File – Write security alerts to a file.
Q6. What are the key benefits of AppRadar™?
A6. Unlike other network-based security solutions, AppRadar™'s host-based server architecture uncovers the relationships between the SQL and eliminates the risk of SQL hidden on the wire using hex encoding. From its position on the host, AppRadar™ can analyze all of the incoming SQL, applying AppSecInc's knowledge base of invalid SQL use to identify parsing errors and invalid logins.
Q7. Firewalls and Intrusion Detection Systems already secure my network. Why do I need AppRadar™?
A7. While firewalls offer perimeter security to your company's network, it is a well-known fact that the determined attackers bypass them – not to mention Web traffic, encrypted traffic, insiders and so on. Similarly, techniques like SQL injection pass requests through a firewall compromising the database. Finally, perimeter defenses never inspect usage by internal users who may be launching attacks or otherwise misusing systems. Traditional security solutions can not stop attacks against databases for the following reasons:
They do not have the intelligence built into them to identify these attacks.
- These attacks exist in a “layer” that is not secured by traditional security solutions and tools.
Many application attacks are performed by insiders already behind a firewall or who are able to evade traditional security solutions.
Q8. Is there a way to create reports of all events captured by AppRadar™ Sensors?
A8. Reports of current and archived events can be generated easily using the AppSecInc Console. Users can easily establish which events are to be collected from each Sensor, and the time frame of events to be included within the report.
Q9. Does AppRadar™ include predefined security policies? Are they customizable? Can I save them?
A9. Policies are sets of security checks that AppRadar™ uses to define what it considers a security event. Events can include intrusion attempts or other malicious behavior. AppRadar™ provides predefined security policies that you can customize and save according to the needs/requirements of your organization.
Q10. Will AppRadar™ affect my current internal application environment? Enterprise Resource Planning (ERP) applications? E-Commerce?
A10. No. AppRadar™ will not have any direct affect on applications, including e-commerce applications, or ERP systems.
Q11. How often is the vulnerability database updated?
A12. The application vulnerability database is updated monthly. These updates are packaged as Application Security Automatic Protection Updates (aka ASAP Updates), and are available to AppRadar™ customers all over the world so that they can secure their mission-critical applications. A complete history of all the ASAP Updates and their respective descriptions can be found on the Application Security, Inc. website at:
ASAP Updates
http://www.appsecinc.com/asap/updates/
A complete listing of all the database attack rules and categories included within AppRadar™ can be found on the Application Security, Inc. website at:
AppRadar™ Attack Categories and Rules
http://www.appsecinc.com/products/appradar/mssql/events-attacks.html
Support
There a four methods of support:
- Toll Free: 1-866-9APPSEC (1-866-927-7732)
- Fax: (212)947-8788
- E-Mail: support@appsecinc.com
- Additional documentation pertaining to AppRadar and the AppSecInc suite of security products is available on the Application Security, Inc. website located at http://www.appsecinc.com.
Conclusions
AppRadar™ is very comprehensive with the policies, rules, and rule categories it provides. It is perfect for the large enterprise that needs database security to dig deep into the source of your SQL server databases.
AppRadar™'s
version level is 1.1.0.1, and it feels like a version 1 product. There were a few things I didn't like about the product:
- It's expensive!
- The application interface is designed for a screen resolution of 1280x1024. Viewing it with anything less creates some issues. This is most apparent in the Alerts screen. Buttons, Check Boxes, etc. fall off the screen to the right. This is most irritating when you are trying to find the "Apply Filter" button.
- The Exceptions screen lacks clear instructions for setting up the conditions (need to demonstrate an example), and it needs to allow you to choose Windows user accounts by using Active Directory Services Interface (ADSI) scripts so you don't have to know the exact username. It also needs to allow you select multiple user names/conditions in one statement.
- Reporting is VERY sad. "The reporting facility in this version of AppRadar is still a work in
progress. In the next version, this will be more developed that will be
able to handle larger amounts of data, such as the report you are creating
now." It took me five minutes to have the application generate a report for one day of alerts. Trying to drill down into Audits for that day's report took 10 minutes. Also, there is no option to export reports to HTML, PDF, TIFF, Excel, XML, CSV, etc.
Comments from AppRadar:
- Comment: Compared to other IDS/IPS systems (specifically in the database space (Lumigent/Entegra/Okena), our pricing is aligned with their models.
- Comment: We are aware of the difficulties associated with the current screen resolution in the tested version and have changed the screen resolution to 1024x768 in our next release.
- Comment: In efforts to address this issue, we are currently revamping our exceptions and audits into the filters sections. We have improved instructions on how to create exceptions as well as audits as well as the advanced section to create new filters/rules.
- Comment: In the version tested, we agree our reporting facility still needs more components to perform better. In the next version, we are adding additional criteria to our reporting wizard that will assist the user to report on a more focused group of data. Also the use of a more limiting policy (not the full policy) would generate smaller amounts of data.
Ratings
I will rate each of the following using a scale from 1 to 5. 5 being the best
and 1 being the worst. Comments are in the last column.
| Ease of Use | 4 | Screens need to be more user centered. COMMENT: Screen resolution is changed to 1024x768 in the new version. |
| Feature Set | 3 | Reporting is seriously lacking in this product. Especially, it needs exporting capabilities. COMMENT: It seems reporting was the only “feature” really evaluated in this review. AppRadar’s ability to as an Audit tool is just one component, as the review showed. What was failed to be pinpointed was AppRadar’s ability to detect malicious activity (ie. Buffer overflows and web application attacks including SQL injection and cross-site scripting), separating our solution from other vendor products in the space. |
| Value | 4 | This product is not for the small shop. Pricing is per agent license (annual) and by console license (perpetual) - 20% each year for maintenance. COMMENT: Evaluating value of a product is tough. The need for AppRadar definitely needs to fit the business requirements and security policies of an organization. The ability to provide an in-depth audit trail, as well as detect malicious behavior on your SQL Servers (where company assets are stored), will continue to be of importance with mounting industry and regulatory requirements, and truly show the importance of value for AppRadar. |
| Technical Support | 4 | Request for an evaluation version (submitted on a Monday) was not fulfilled until, on Friday, sqlservercentral.com contacted them to request a copy for this review. Don't expect an immediate response. EDITORS NOTE: This one was my fault. I was coordinating between the vendor and reviewer and did not respond to things in a timely manner. Once I clarified the reviewer with AppRadar, they issued a key immediately. |
| Lack of Bugs | 5 | None found (yet). |
| Documentation | 3.5 | Needs to include screen shots and examples but content is comprehensive. COMMENT: Most of the review was taken from our documentation. The reviewer acknowledges the comprehensiveness of our documentation. Adding screen shots in the user guide will be noted. |
| Performance | 3 | Reports take forever. Application response is slow at times. COMMENT: It seems our performance was strictly measured by our reporting facility. In an organization, what is important is AppRadar’s performance in capturing alerts during normal SQL application usage. Metrics conclude AppRadar affects the speed of query execution by less than 1/1000th of a second per query while using the Full Policy. |
| Installation | 5 | Easy enough. |
| Learning Curve | 4 | Takes a few "What the...?" on some of the screens. |
| Overall | 3.94 |
Product Information
Web Site: http://www.appsecinc.com/products/AppRadar/
Developer: Application Security, Inc.
Pricing:
AppRadar™ is licensed accordingly:
- Database Sensor Licensing
- Microsoft SQL Server 2000: Annually per instance
- AppSecInc Console
- Per Machine Installation (perpetual license)
- Per User (Console initially comes with a 5 User Pack)
- 20% yearly maintenance fee
You can purchase AppRadar™ by calling 1-866-9APPSEC or by sending an email to sales@appsecinc.com.

