Introduction
Cloud Computing escalates the security risks of an organization. This happens because of the extended trust boundary associated with deploying IT assets beyond the data centers of the asset owners. The trust boundary exposes organizations to such risks as internal malicious actors, man-in-the-middle attacks, ransomware attacks, and more. In order to mitigate these risks, cybersecurity experts have come up with frameworks to address cloud security - risks related to unauthorized access and risks related to the data breach.
In this article, we shall discuss a three data-oriented security mechanisms developed by cloud service providers and give examples of how AWS implements mechanisms to mitigate the risk of data breaches.
Basic Terminology
The following terms are used in this article and thus need to be clarified. These definitions are sourced from resources available from Arcitura and other experts on cloud security.
Malicious intermediary - This refers to a security threat that arises when messages are intercepted and altered by a malicious service agent. The confidentiality and/or integrity of the message are hereby compromised. The malicious agent may also insert harmful data into the message before forwarding it to its destination.
Trust Boundary - A trust boundary is a logical perimeter that typically spans beyond an organization's physical boundaries. It represents the extent to which IT resources are trusted. If physical IT resources within a cloud are shared by different cloud service consumers, these cloud service consumers have overlapping trust boundaries. Malicious cloud service consumers can target shared IT resources with the intention of compromising cloud consumers or other IT resources that share the same trust boundary.
Authentication - This is the process of verifying the identity of a user or device requesting access to a resource. Authentication is typically achieved using a variety of techniques, such as challenging the requester to supply something they know, something they have, something they are, or any combination of these elements. These are referred to as the three factors of authentication.
Authorization - The process of granting or denying access to resources based on the identity of the user or machine. Authorization is achieved through a variety of mechanisms, such as access control lists (ACLs), role-based access control (RBAC), and attribute-based access control (ABAC).
Authentication and authorization are two of three common combined processes for controlling access to computing resources. The third "A" in this "AAA" trinity is accounting. One can think of these three processes as asking basic questions:
- Authentication - Who are you?
- Authorization - What can we let you do?
- Accounting - What have you done?
This resource from Kansas State University provides a useful set of definitions for basic cybersecurity terms. Arcitura provides more elaborate discussions of these concepts as well.
Cloud Security Mechanisms
This section does not discuss all security mechanisms. We focus on three data-oriented security mechanisms specifically: encryption, hashing, and digital signatures. We consider these mechanisms data-oriented because these mechanisms focus on protecting data at rest, in motion, or in use rather than just controlling access to the systems where such data is stored.
Encryption
Encryption is the process of converting data into a code or cipher that can be securely transmitted or stored without being accessed by unauthorized users. It is critical to the protection of sensitive or confidential information from interception or theft.
Encryption mechanisms are mathematical algorithms that transform the original plaintext into ciphertext - the encrypted form of the data. These algorithms apply keys to plaintext to produce ciphertext. The same key must be used to decrypt the ciphertext back into plaintext. An encryption algorithm could be symmetric or asymmetric. Symmetric key encryption algorithms use the same key for both encryption and decryption, while asymmetric key encryption algorithms use a public key for encryption and a private key for decryption.
The encryption mechanism mitigates the following security threats:
- Malicious intermediary - confidentiality of message data received is protected
- Insufficient Authorization - Will protect the confidentiality of the message data is protected if the intention of the intermediary is to steal message data
- Overlapping trust boundaries - Encryption can be applied to data exchanged or residing within overlapping trust boundaries preventing access by attackers that exploit these trust boundaries.
Hashing
Hashing is a process of converting data into a fixed-size key that represents the original data in a unique and irreversible manner using a mathematical algorithm. The output of this process is a hash value or digest.
Hashing is commonly used in computer science and information security to validate data integrity, store passwords securely or create digital signatures. Common hashing algorithms include MD5, SHA-1, SHA-2, and SHA-3.
Digital Signatures
A digital signature is created by applying an algorithm to a document or message, which produces a hash. The hash value is then encrypted using the sender's private key, which creates a digital signature that can be attached to the data being sent. The recipient can then use the sender's public key to verify the digital signature and confirm that the data was not altered during transmission. In other words, Digital Signatures combine encryption and hashing to secure data.
Digital signatures provide several benefits, including:
- Authenticity: Digital signatures verify that the sender of the message or document is who they claim to be.
- Integrity: Digital signatures ensure that the document or message has not been tampered with or altered during transmission.
- Non-repudiation: Digital signatures provide proof that the sender cannot deny sending the document or message.
Digital signatures use encryption and hashing. If the contents of a message are altered, the digital signature is invalid.
- Malicious intermediary - the integrity of message data received by intermediaries is protected
- Insufficient Authorization - The use of DS provides a means to detect alterations if an attacker modifies the message
- Overlapping trust boundaries - Digital Signatures can be applied to data exchange within overlapping trust boundaries and between IT resources.
Cloud Security Mechanisms in AWS
Amazon Web Services (AWS) provides data-oriented cybersecurity capabilities through their wide range of services. Some services are designed to deliver these security mechanisms, while others have the mechanisms built in as part of the service to ensure data is secure.
Providing AWS Data-Oriented Security Mechanisms.
Here are some AWS Services that provide data-oriented security mechanisms to protect your data.
Amazon KMS (Key Management Service)
KMS is a managed service that provides a centralized key management system for encrypting data in various AWS services. It offers a secure and scalable way to create, manage, and use encryption keys.
AWS Secrets Manager
Secrets Manager helps you protect secrets, such as database credentials and API keys, by storing and managing them securely. It provides encryption of secrets at rest and in transit, as well as automatic rotation of secrets for better security.
AWS CloudHSM (Cloud Hardware Security Module)
CloudHSM provides dedicated hardware security modules to protect sensitive data by providing secure key storage and cryptographic operations. It is a fully managed service that helps you meet regulatory and compliance requirements.
AWS Services that Leverage Data-Oriented Security Mechanism
The following services leverage the security mechanisms to improve data security.
Amazon S3 (Simple Storage Service)
S3 provides multiple security features for data protection, including server-side encryption with Amazon S3-managed keys, client-side encryption, bucket policies for access control, and access logs for audit trails.
Amazon RDS (Relational Database Service)
RDS offers security features such as encryption at rest, SSL/TLS encryption for data in transit, IAM database authentication, and VPC security group for network access control.
Amazon Redshift
Redshift provides multiple security features, including encryption at rest, SSL/TLS encryption for data in transit, IAM authentication for user access control, and VPC security groups for network access control.
Encryption Options in Amazon S3
When you create a bucket in Amazon S3, you are given the option of Amazon S3 managed Keys or AWS Key Management Service. Both of these options are sub-sets of Server-Side Encryption which is the default for Amazon S3 (See Figure 1). According to AWS, starting January 2023, all new object uploads to Amazon S3 are "automatically encrypted at no additional cost and with no impact on performance".
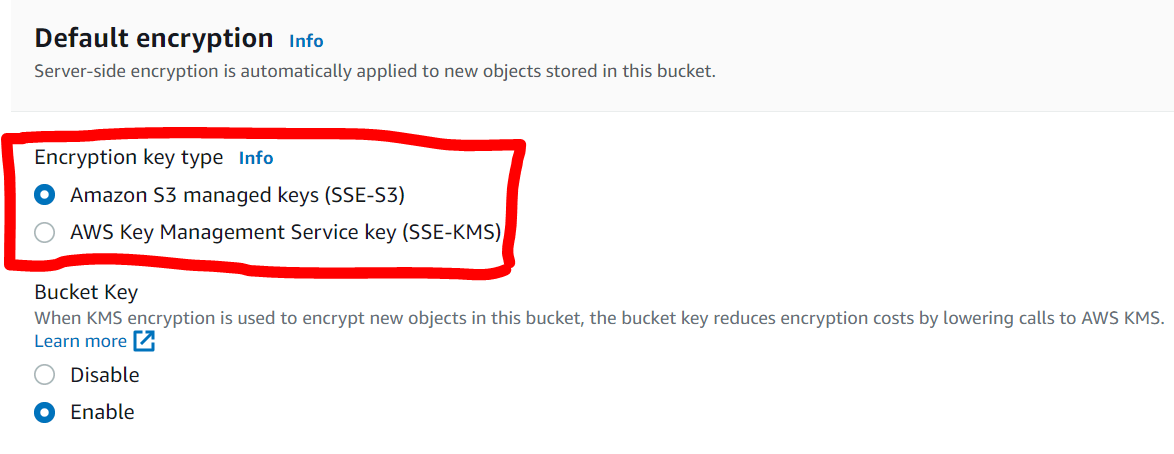 Fig. 1: Default Encryption in Amazon S3 (SSE-S3)
Fig. 1: Default Encryption in Amazon S3 (SSE-S3)For both Amazon S3 Managed Keys and AWS Key Management Service, you can choose to enable or disable Bucket Key. AWS gives useful advice on how to reduce encryption costs by making sure you use S3 Bucket Key for SSE-KMS in this article. In other words, Bucket Key is better left enabled.
When you choose SSE-KMS, you can choose to use the default AWS KMS Key (aws/s3, See Figure 2), pick existing keys from KMS (customer-managed keys you created earlier) or create a new KMS Key. In both cases, encryption keys managed in KMS must be in the same region as the S3 bucket.
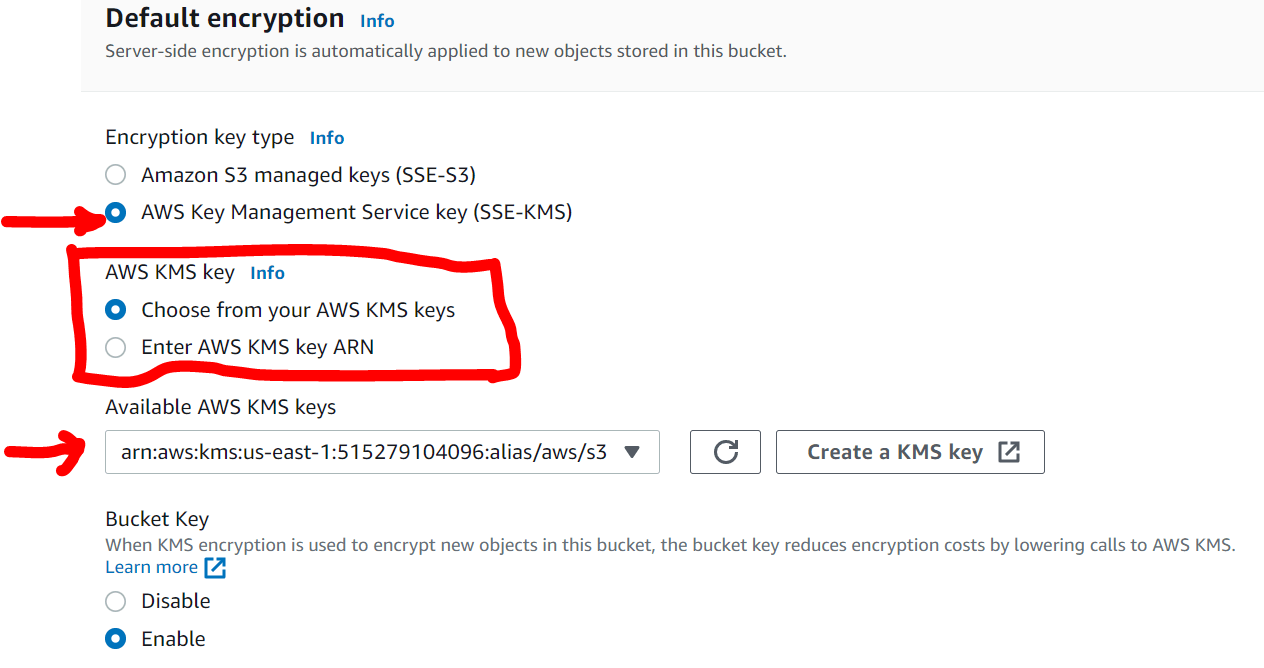 Fig. 2: Encryption Key Type - AWS Key Management Service
Fig. 2: Encryption Key Type - AWS Key Management ServiceThe alternative to selecting an existing KMS from a drop down menu is explicitly typing the Amazon Resource Name as shown in Figure 3.
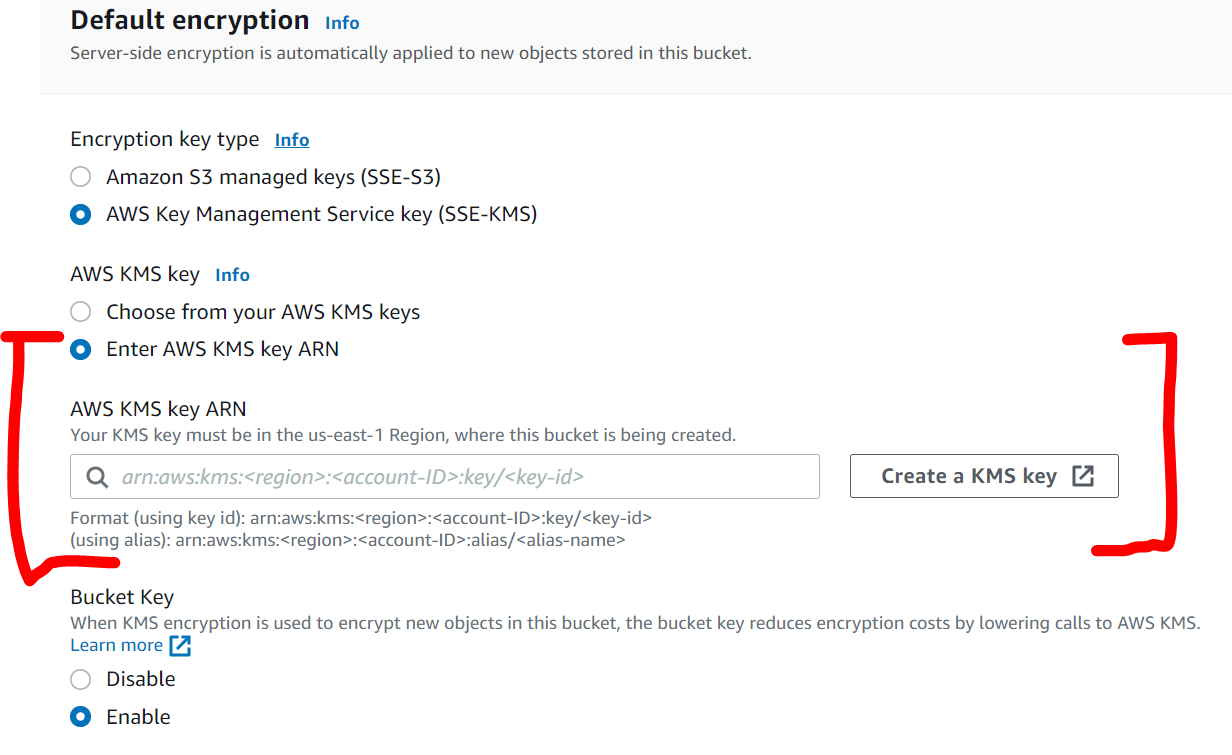 Fig. 3: Explicitly Define a Key Using an ARN
Fig. 3: Explicitly Define a Key Using an ARNEncryption Options in Amazon RDS
AWS also provides options for encrypting databases created in RDS. In Amazon RDS, encryption is configurable at the point of creating databases (See Figure 4). Similar to Amazon S3, Amazon RDS also depends on AWS KMS for manage keys. The default key is /aws/rds but one can specify the ARN for an encryption key explicitly as well (see Figure 5).
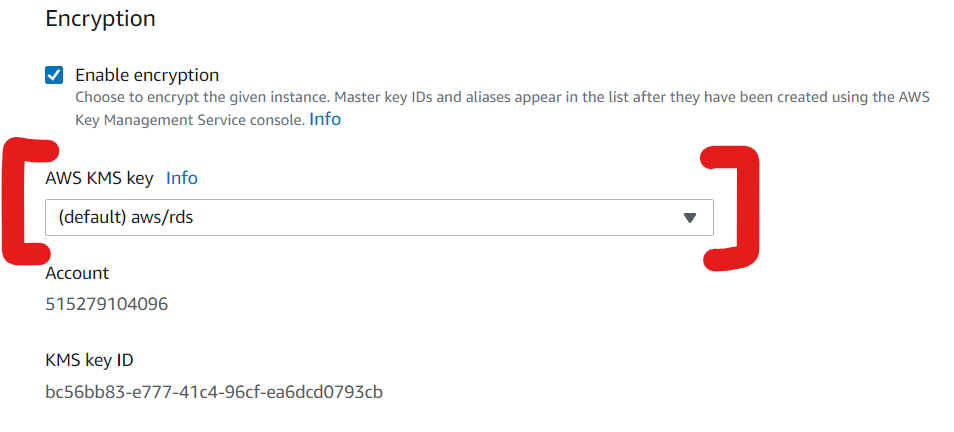 Fig. 4 Encryption in Amazon RDS
Fig. 4 Encryption in Amazon RDS
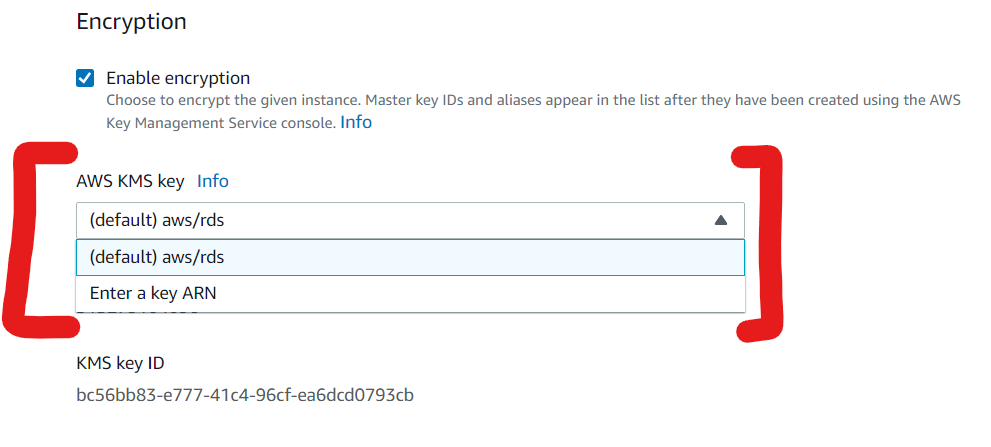 Fig. 5 Amazon RDS Encryption Options
Fig. 5 Amazon RDS Encryption OptionsAWS has simplified the process for setting up encryption for databases. However, the concepts are essentially the same as if one were configuring encryption using native commands such as is possible in both MS SQL Server, Oracle and others or using interesting tools like dbForge SQL Complete or IBM Guardium .
Encryption in AWS - Additional Information
A block cipher is a type of encryption algorithm that encrypts data in fixed-size blocks, typically 64 or 128 bits in size. The block cipher takes in plaintext data and transforms it into ciphertext by applying a series of mathematical operations using a secret key.
AWS uses some of the strongest block ciphers available for encryption, including the 256-bit Advanced Encryption Standard (AES-256), Triple Data Encryption Standard (Triple DES), and Secure Hash Algorithm 3 (SHA-3). The strongest of these algorithms is AES-256. The number 256 refers to the length of the encryption key in bits. It also implies that the possible number of keys that AES can generate is 2^256 meaning it is virtually impossible to break using brute force attacks.
SHA-3 is a more recent version of cryptographic hash algorithms discussed earlier as useful in digital signatures, password storage, and message authentication. SHA-3 supports four output sizes: 224 bits, 256 bits, 384 bits, and 512 bits, and is also used in combination with AES-256.
Conclusion
This article focused on data-oriented cloud security mechanisms. Cloud Service Providers such as AWS have done a great job of implementing these mechanisms as services that can be consumed by their clients and as capabilities that protect clients' data on their other cloud services, as is the case with Amazon S3. Cloud service consumers do themselves a great favor by exploring and properly utilizing these security mechanisms in whatever cloud platform they opt for.


