Review of NGSSquirrel for SQL Server
by Dale Elizabeth Corey, July 6, 2004

Introduction
NGSSquirrel is a security auditing product for SQL Server developed by Next Generation Security Software Ltd in the United Kingdom. NGSSquirrel is part of NGSSoftwares' suite of Intelligent Next Generation Security Assessment tools. Other products in the suite include:
- Typhoon III - an intelligent vulnerability scanner
- NGSSQLCrack - password cracking tool for Microsoft SQL Server (this comes with the NGSSquirrel or can be purchased separately)
- NGSSquirrel for Oracle - security auditing tool for Oracle Database Server
- OraScan - a security tool specifically designed for auditing custom Web applications
- Domino Scan II - security auditing tool designed for Lotus Domino Web Server
- NGSSniff - a free program designed to capture and analyze network data packets
NGSSquirrel for SQL Server is a vulnerability assessment scanner. It allows
system administrators and security professionals to quickly and easily
assess SQL Servers (7 & 2000) for a variety of security vulnerabilities and
deficits. The NGSSquirrel security scanner comprehensively scans SQL Servers for
hundreds of possible security threats.
NGSSquirrel was developed by a group of security researchers. It allows
authorized users to quickly find the faults and weaknesses in their database
environment before malicious attackers do. NGSSquirrel allows system
professionals to quickly and accurately assess the level of risk that their
servers are exposed to, and then if required, fix all discovered
vulnerabilities with ease, not just discover the "holes" (i.e., Microsoft's Baseline Security Auditor and SQL Scan).
NGSSquirrel includes the ability to generate lockdown scripts which will secure the server based upon the vulnerabilities discovered.
The benefits and features of NGSSquirrel include:
- BUILTIN\Administrator XSTATUS, checking sysxlogins tables
- Start-up procedures, stored procedure checks
- Fixes vulnerabilities by generating lockdown scripts
- Flexible with three levels of audit (quick, normal and full)
- Up-to-date, updateable with newly discovered vulnerabilities
(i.e., scans for unpublished vulnerabilities that have been discovered by the NGS security research team)
- .NET Capable, compatible with Microsoft .NET Server (RC1)
- Multiple output formats for scan results (plain text, HTML, DHTML, rich text format, MS Excel, or written to SQL)
By August 2004, NGSSoftware will be adding NSM (NGSSquirrel Security Manager) to NGSSquirrel for SQL Server. This is already integrated in the NGSSquirrel for Oracle product. This product allows consumers to manage user and role privileges (create/drop user, change user password, create/drop role, and change role password), manage system privileges (grant/revoke/search), and manage object privileges (grant/revoke/search). Logging enables the user to have the ability to undo actions.
Pricing of the NGSSoftware pricing is dependent on the end users requirement of use and is priced accordingly.
Pricing is in Great British Pound. The equivalent USD is calculated at today's £1 GBP = $1.84 USD, therefore USD is changeable depending on the exchange rate at the time.
Enterprise license - per installation/copy
Squirrel for SQL Server (Total amount of SQL servers hosted):
1-5 server network - £1,495.00 GBP, ($2,750.00 USD)
6-10 - £1,995.00 GBP, ($3,670.00 USD)
11-20 - £2,495.00 GBP, ($4,590.00 USD)
21-30 - £2,995.00 GBP, ($5,510.00 USD)
31-50 - £3,495.00 GBP, ($6,430.00 USD)
50+ Open license- £3,995.00 GBP, ($7,350.00 USD)
Consultant license
SC - £3,995.00 GBP, ($7,350.00 USD)
Don't forget, NGSSQLCrack is supplied Free along with NGSSquirrel for SQL Server. You will need to request a license key for this tool as well. NGSSQLCrack is also marketed as a separate product and is sold for £250.00 GBP, ($460.00 USD).
Because of the exchange rates, etc., you really should contact NGSSoftware to firm up the pricing information by emailing sales@ngssoftware.com or sales@ngsconsulting.com.
Environment
NGSSquirrel for SQL Server can be used with the following operating systems:
- Microsoft Windows 2000
- Microsoft Windows XP
- Microsoft .NET Server (RC1)
- Microsoft Windows NT Version 4.0 (Service Pack 4)
Minimum Recommended Computer Specification:
- Pentium 3 (500MHz)
- 128MB RAM
- 5MB free disk space for program
Installation
Installation of the product itself was fast and easy. It consisted of a license agreement, specifying customer information (user name and organization as well as whether it can be installed for all users or for the designated user name only), and specifying a destination location.
Once the product is installed and you open NGSSquirrel for the first time, you will be asked to activate your license (see Figure 1 below). This is a bit time consuming because, for security reasons, you will have to copy the license block the installation generated into an email and then send it to licenses@ngssoftware.com. Then, you have to wait for NGSSoftware to respond with the activation key. As general practice, the license request and activation is done within 24 hours (Mon-Fri standard, weekends subject to work load), but usually occurs within hours of the request. Time zone differences need to be taken into account as well.
Figure 1
Using NGSSquirrel for SQL Server
When you open NGSSquirrel, you will see the following window (Figure 2):
The main menu consists of the following options:
![]()
File
- Open (hotkey Ctrl+O ), allows the user to access a previous scan (from compatible files ending in the extension *.ngs)
- Save (hotkey Ctrl+S ), allows the user to save a scan to a file for later use
- Export Report to... allows the user to export the current scan report into the format of choice ( Text File, HTML (static or dynamic), Rich Text File or ODBC Data Source)
- Generate Lockdown Script(s) (hotkey Ctrl+G ), allows the user to generate a lockdown script for the selected host(s) or selected vulnerabilities
- Print Report (hotkey Ctrl+P ), allows the user to print the results of the current scan
- Exit (hotkey Alt+F4 ) allows the user to quit the NGSSquirrel for SQL Server program
Edit
- Authentication Details , allows the user to specify usernames and passwords to be used whilst scanning the host. This option is also available from the Right Click Menu.
- Connection Test Settings , allows the user to perform a test on a range of hosts to see which ports are open
- Audit Options , allows the user to select the level of scan to be performed on the host.
- Purge Host (delete from tree) , allows the user to remove the scan information for the selected host in the left hand pane. This option is also available from the Right Click Menu.
View
- Refresh , allows the user to refresh the information screen for the current scan
Scan
- Add Hosts (hotkey F2 ), allows the user to select the host(s) to be scanned for vulnerabilities
- Start Scan (hotkey F6 ), allows the user to start scanning the selected host(s). This option is also available from the Right Click Menu.
- Stop Scan (hotkey F7 ), allows the user to cancel scanning the selected host(s)
- Resume Scan (hotkey F8 ), allows the user to continue a scan after executing the Stop Scan command
- Connection Test , allows the user to perform a connection test on the current host(s)
Tools
- Launch Program allows the user to open Query Analyzer, the Command Prompt or Notepad without leaving the main screen
- Execute selected text (hotkey F10 or Alt+X ), allows the user to execute user generated queries
Help
- Index (hotkey F1 ), allows the user access to this compiled HTML help file
- About , displays the version number & license information for this copy of NGSSquirrel for SQL Server .
The toolbar buttons on the main menu have the following functions:
![]()
- Select SQL server to Audit
- Open Scan File
- Save Scan File
- Start Scan
- Stop Scan
- Generate SQL Server Lockdown Script
- Launch Query Analyzer
- Open Notepad
- Open a Command Prompt
- Help
Scanning with NGSSquirrel
To run a scan, you need to choose Scan/Add Hosts from the main menu to bring up the Add Hosts screen (see Figure 3 below). You can select a single host or a range of hosts.
When selecting a broad range of hosts, NGSSquirrel for SQL Server can run a connection test in order to establish which IP addresses in the selected range have ports open and available for scanning (this is recommended). You can specify specific ports to scan under the Edit/Connection Test Settings menu after you add the hosts.
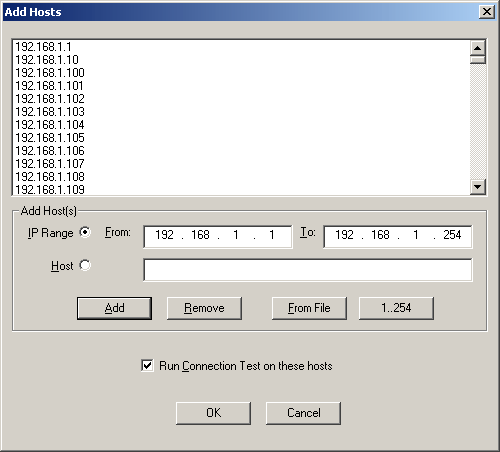
Figure 3
After the hosts are added, you will be returned to the main screen. The detected hosts will be listed in the left panel (Figure 4).
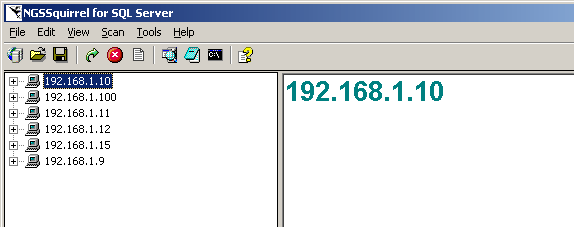
Figure 4
You will then need to specify the authentication details under Edit/Authentication Details (Figure 5). You even have the option to use the password dictionary that is part of SQLCrack.
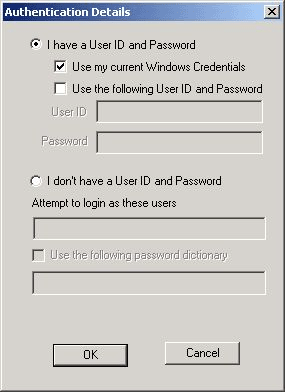
Figure 5
You can specify ports to scan by selecting Edit/Connection Test Settings from the menu. You can also specify runtime audit options by selecting Edit/Audit Options from the menu (Figure 6).
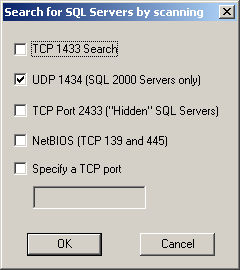 | 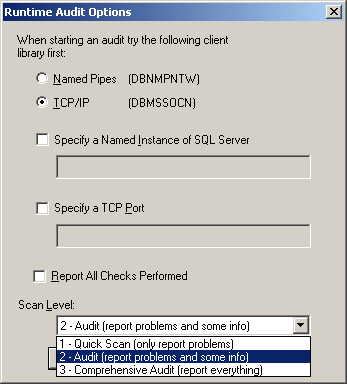 |
Figure 6
After the Authentication Details are specified (and any specific ports are set under Edit/Connection Test Settings), you can start the scan by clicking Scan/Start Scan from the menu or right clicking on a host and choosing Scan Hosts. You can view the Status bar at the bottom of the screen to watch the progress (Figure 7). You will see a message, "Scan Succeeded", in the right panel appear (Figure 8) when it's finished. The status bar
is divided into three areas. The left hand block indicates the process which is currently running and the middle block gives an indication of the progress for the whole scan (the right hand block has not been designed to contain any information).
![]()
Figure 7
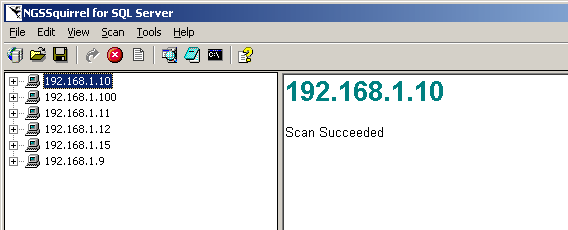
Figure 8
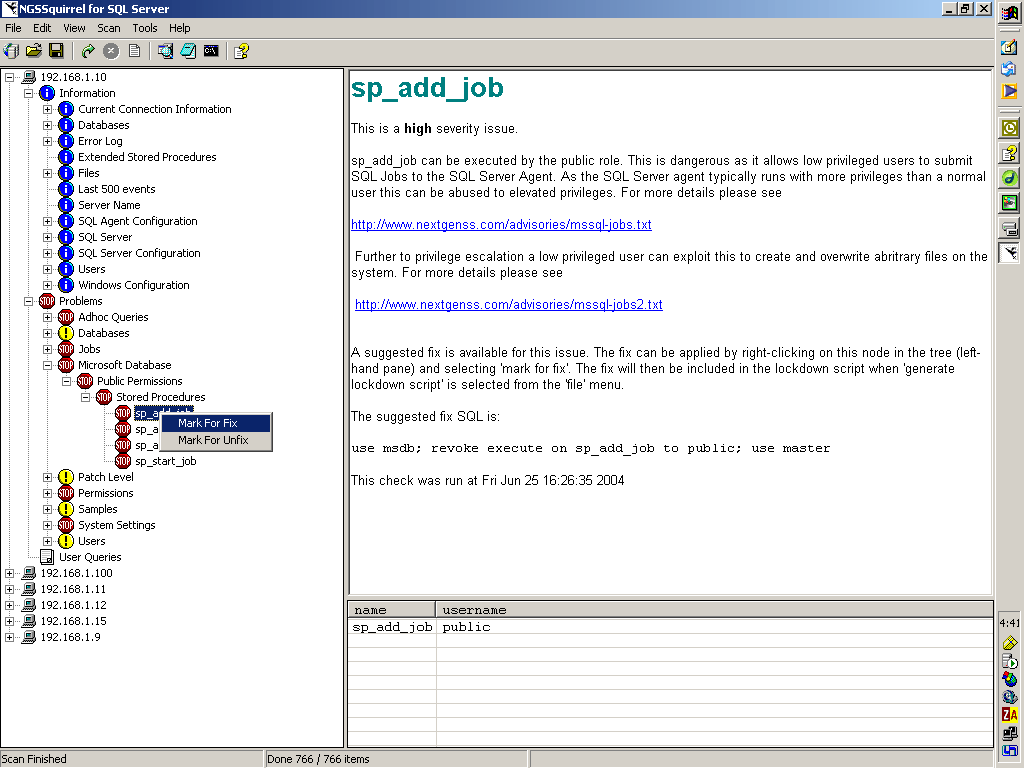
After the scan is complete, you can view and analyze the results of the scan by clicking the plus sign (+) next to the host name (Figure 9). Once the results are expanded, you will see them divided into three sections: Information, Problems, and User Queries.
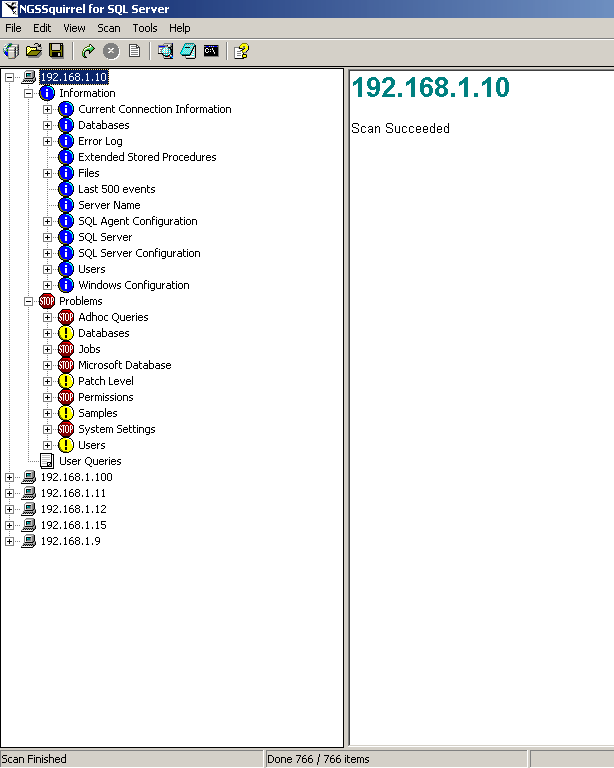
Figure 9
The icons displayed indicate the following:
Indicates a host
Indicates issues which have been evaluated as a HIGH SEVERITY RISK
Indicates issues which have been evaluated as a MEDIUM SEVERITY RISK
Indicates issues that are for informational purposes only (these are "nice to know" items)
Indicates User Queries which are customizable
Once the problem areas are identified, you can look further into the details of the problem by clicking on the specific item (Figure 10). If the fix is a patch, you will be given a hot link to the patch.
Figure 10
The NGSSquirrel for SQL Server display window is separated into two panes. The left hand pane behaves much like the folder view in Windows Explorer. You can expand and contract the details using the plus and minus symbol respectively. Clicking on an icon in the left hand pane will display the relevant details in the right hand pane.
The right hand pane itself can also be split horizontally for sections which need to display additional information. This can include the contents of the relevant file(s) or information retrieved from the host during the course of the scan.
You can right click on an item to "Mark for Fix" suggested in the right pane. Once an item is marked for a fix, a green check mark with show up beside it (Figure 11). You can also "Mark for Unfix".
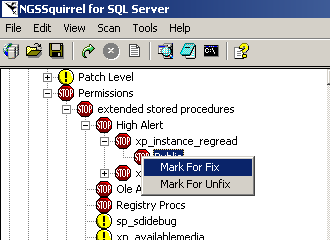 | 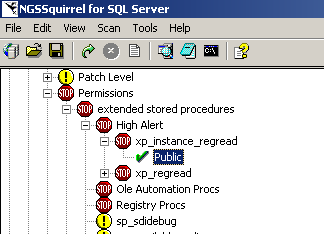 |
Figure 11
To initiate the fixes, you will need to select File/Generate Lockdown Scripts from the menu (Figure 12).
Not all vulnerabilities are available to the lockdown script since some may require specific manual intervention to rectify (i.e. downloading a security patch ).
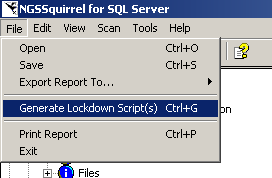
Figure 12
The lockdown script will then appear in the right hand pane (Figure 13).
These files are stored in SQL Script Files format (*.sql).
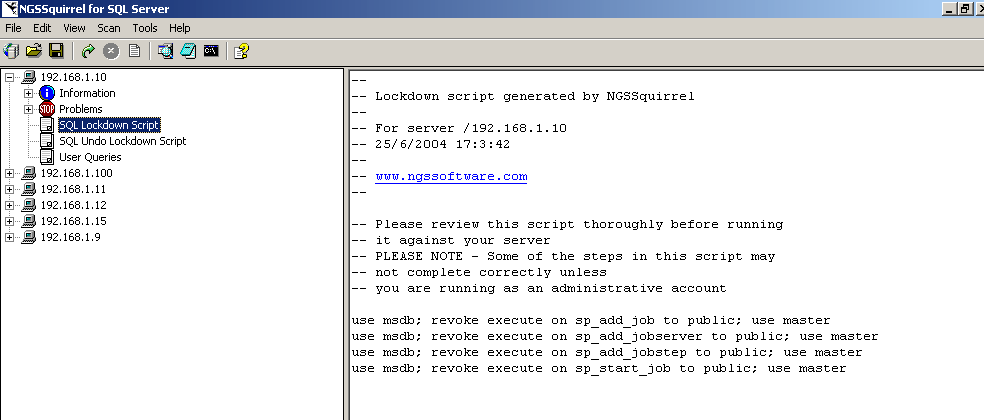
Click for Full size image.
Figure 13
You can run the scripts by highlighting the text and then pressing Alt+X or F5, or if you want, you can launch Query Analyzer from the toolbar or from the Tools menu and execute the script from there (Figure 14).
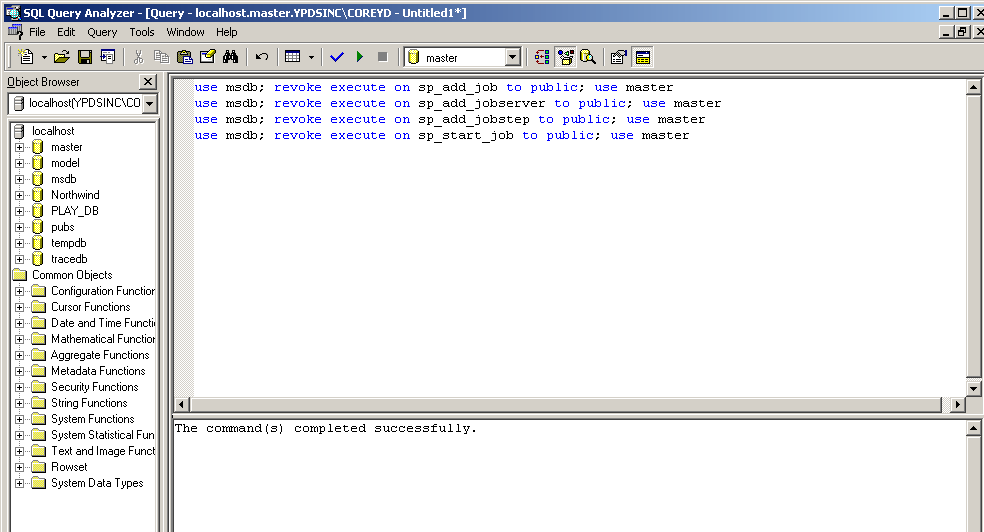
Figure 14
The nice thing is that you also get an Undo Lockdown Script in case this isn't what you wanted to do (Figure 15).
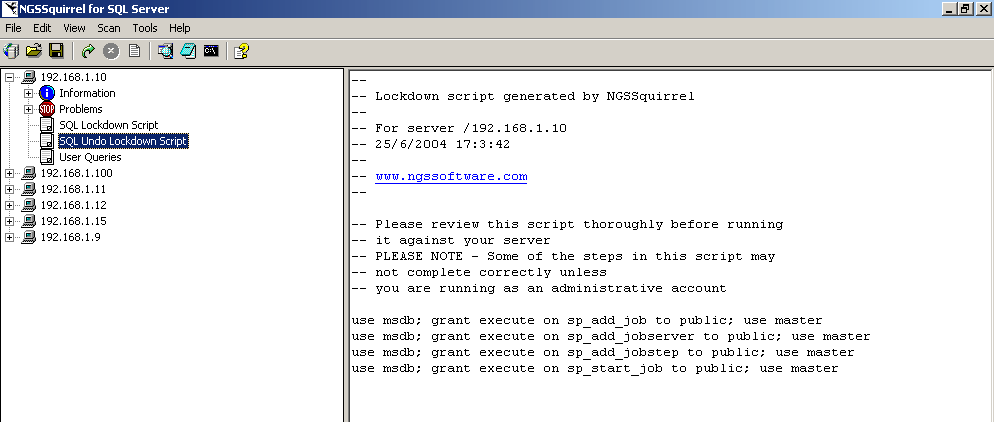
Click for full size image.
Figure 15
Additional Features
- NGSSquirrel utilizes an alternate right click menu for items (Figure 16).
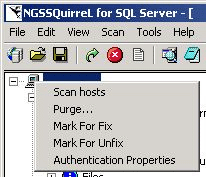
Figure 16
2. NGSSquirrel provides the following command line interface (Figure 17):
Usage: NGSSQUIRREL host [options]
Where the following options are available:
- /port:[port] default 1433
- /user:
- /pass:[password] default (blank)
- /netlib:[namedpipes, tcpip] default tcpip
- /instance:[instance name]
- /level:[1,2,3] default 2
- /report:[html,rtf,txt] default html
- /reportdir:[report destination directory] default (current dir)
- /reportname:[report name] default (current date)
If no username and password are provided (or invalid) NGSSquirrel for SQL Server attempts to connect using a default account.
The report destination directory and report name cannot contain any spaces.
Where no switch has been specified the default value is automatically used.
This information can be accessed by typing the following into the command line:
NGSSQUIRREL /?
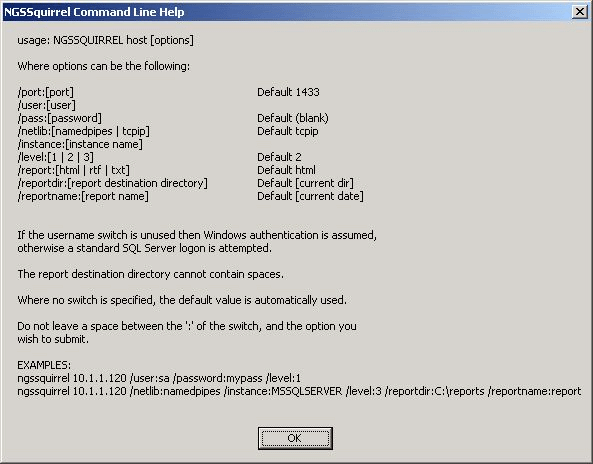
Figure 17
3. NGSSquirrel provides the following external tools (Figure 18):
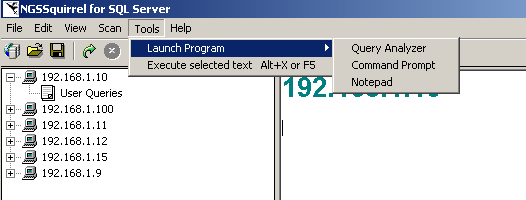
Figure 18
4. NGSSquirrell will allow you export reports in the following formats (Figure 19):
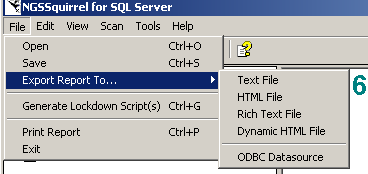
Figure 19
NGSSquirrel Frequently Asked Questions
[Q1]: Does NGSSquirrel for SQL Server determine the patch level for MS SQL server?
[A1]: NGSSquirrel for SQL Server determines the patch levels of MS SQL servers to a low level and includes whether or not the required hot fixes have been applied.
[Q2]: Can you compare results of a new scan with a previous scan?
[A2]: At present this functionality has not been implemented.
[Q3]: Can NGSSquirrel for SQL Server be launched from within a script?
[A3]: Yes. NGSSquirrel for SQL Server can be launched from the Command Line Interface , so scans may be initiated from within a script.
[Q4]: Is the checking for vulnerabilities and errors dependant on the available bandwidth?
[A4]: NGSSquirrel for SQL Server will eventually timeout if responses to queries are not received (the timeout is quite generous though).
[Q5]: Is it possible to create custom scans? For example, a vulnerability that the scanner rates as medium we may consider to be high. Can these types of items be edited?
[A5]: At present this functionality has not been implemented.
[Q6]: Can NGSSquirrel for SQL Server be used to make scheduled scans and automatically export the results?
[A6]: Yes, using the Command Line Interface .
An example of this would be:
- at 23:00 /every:M,T,W,Th,F,S,Su "C:\Program Files\NGS Software\NGSSquirrel\NGSSquirrel.exe" 127.0.0.1 /user:test /pass:test1 /report html /reportdir C:\reports
Which results in running a scan everyday at 23.00, on the local machine with an HTML report saved to the reports folder on C:\
[Q7]: Each vulnerability has a severity number associated with it, what do these numbers actually mean?
[A7]: As a general rule, a score in excess of 66 indicates a high risk, 33-66 indicates a medium risk and less than 33 indicates low risk or informational issues (where no action is usually required to be taken). As an example, the most serious issues (such as unauthenticated remote compromises) are usually rated as 90+ whilst denial of service issues would be rated from 50+ and misconfigurations (such as no auditing, no shutdown when log full, etc) are generally rated at 30+.
[Q8]: Who decides what severity any given vulnerability is assigned?
[A8]: Check writers at NGS Software define the severity based on their perception of risk. All severities are subject to change and can be upgraded or downgraded where appropriate.
Support
For problem solutions, product announcements, and general information about the use and configuration of NGSSquirrell, you are asked to login to NGSSoftware's customer site. However, when you log in, you are taken directly to downloads.
Alternatively, if additional support is required, you can contact a product support specialist at support@ngssoftware.com.
Conclusions
All in all, this is a great tool for vulnerability assessment. The lockdown scripts (200+) make it worth purchasing. I could not believe all the scripts this product offers. It is by far much more comprehensive than Microsoft's Baseline Security Analyzer. This is definitely a must product for large enterprises.
As for items that need improvement, when Steve Jones rated this product in October, 2002 (http://www.sqlservercentral.com/columnists/sjones/reviewngssquirrel.asp), he suggested a few enhancements that are still not available - custom scans, comparing two scans, and automatic updates. However, the following development plan has been provided and is anticipated to be complete by the end of 2004:
- All products will be database driven, meaning that all checks will be executed based on information in a check database, all output will be sent to a ‘repository’ database and all internal state will be managed within this ‘repository’ database. This will enable NGS to greatly enhance the reporting and scheduling capability of our software, as well as providing us with a mechanism for distributing scans.
- Introduction of a single GUI.
- Provision of historical scan comparisons, i.e. the capability to discover which problems were fixed on a host since the previous scan.
- Greatly improved reporting, links to CVE , unique NGS check ID for every check.
- More detailed information, greater flexibility in managing, recording and monitoring of progress from discovery to mitigation and fixing the problem, through to deliverable- management reporting.
- Customization of scanning able to input individual checks specific to requirements.
- Able to switch on/off any module and individual checks within each module.
- Schedule scanning from a GUI interface (currently offered through CMD line)
There were two problems that I mentioned in my draft review. 1. Right clicking on Scan Hosts did not work. 2. The Add/Remove screen did not refresh the left pane when you removed hosts. You had to physically click on the host and choose Purge from the menu to remove it. These two items have been fixed in the latest version (1.522.0.0, Monday July 5, 2004).
Ratings
I will rate each of the following using a scale from 1 to 5. 5 being the best
and 1 being the worst. Comments are in the last column.
| Ease of Use | 5 | Great after the Add/Remove host feature was enhanced |
| Feature Set | 4.5 | See Conclusion section |
| Value | 4 | For 1 - 5 servers, this product seemed too pricey |
| Technical Support | 4 | Needs to be more comprehensive on the Web site (i.e., provide a knowledge base) |
| Lack of Bugs | 5 | Great after right clicking Scan Host was fixed |
| Documentation | 5 | Excellent! |
| Performance | 5 | Excellent! |
| Installation | 5 | Easy |
| Learning Curve | 5 | Easy |
| Overall | 4.7 |
Product Information
Web Site: http://www.nextgenss.com/squirrelsql.htm
Developer: NGS Software
+44 (0)20 8401 0070.
Pricing: See Introduction section