Learn Continuous Integration for Databases in Bellevue, WA
Redgate Software has teamed up with Northwest Cadence to present a workshop on May 15, 2015. Come learn how to implement continuous integration in your database development software pipeline.







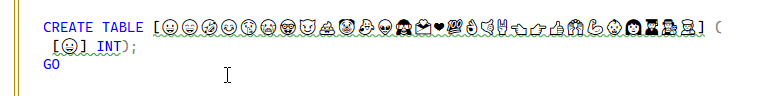 When I check the length, I get these results:
When I check the length, I get these results: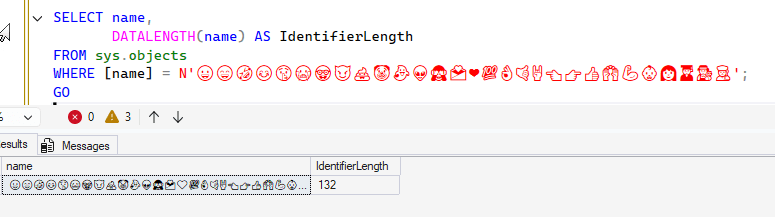 A table name is limited to 128 characters. How does this work?
A table name is limited to 128 characters. How does this work?