NGSSQuirreL
Introduction
I received a copy of this software after my review of SQLCrack. Thanks to David Litchfield and NGSSoftware for the copy. I ran the setup on XP and the install ran flawlessly. I also received a note from NGSSoftware that it has been run on Windows NT and Windows 2000. No testing on Windows 9x, so I'd be interested to see if anyone has tried it there. Alas, none of those machines around my domain anymore.
Running the Program
When you run the program, you will see a simple interface, similar to that of the SQLCrack program. Below is a screen show of the welcome screen. I liked that the welcome screen shows instructions for running a scan in it in easy step by step, making it difficult to mess up the process.
As instructed, I added a server by selecting "Scan | Add Host" from the menu, entered the servername, and hit enter. Whoops, that doesn't work. Go back, hit "Add" this time.
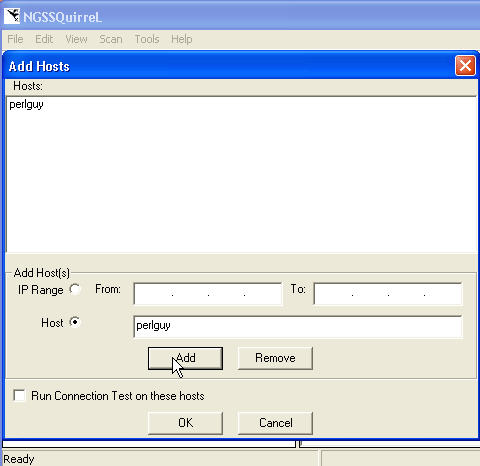
The server is added. Now hit "OK" and I get my server listed in the left hand pane.
The Edit menu allows me to change from Windows Auth (the default as it should be). It's always amazing to me how many products only use SQL Authentication, so I like to point this out. Here are your options.
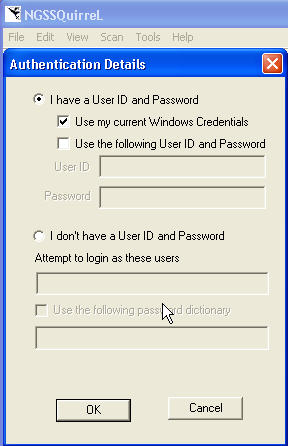
I thought it was very interesting that there is an option to attempt logins with a password dictionary. I didn't try this, but I assume it works leveraging the code from SQLCrack (review), which runs well.
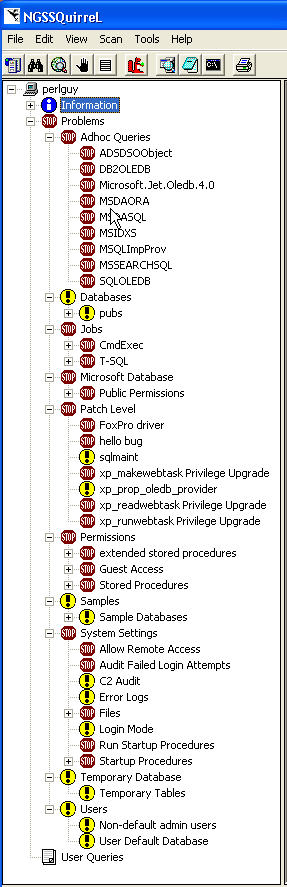
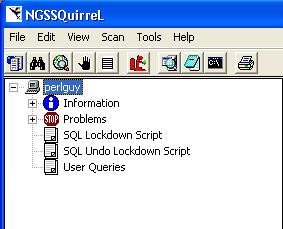
The next step is to start a scan. I did this by selecting "Scan | Start Scan" from the menu. On my test system, connected to a remote SQL Server, this scan ran in about 20 seconds. Once it finishes, you can expand the server name in the left pane to see the results of the scan. The server expands to "Information", "Problems", and "User Queries" sections. My results are shown here:
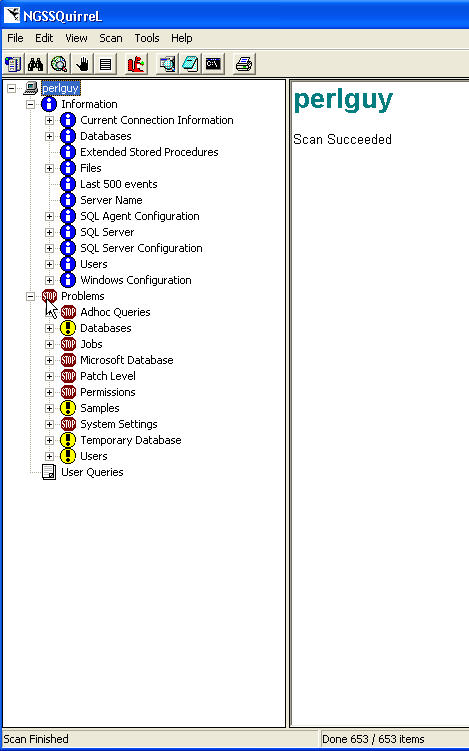
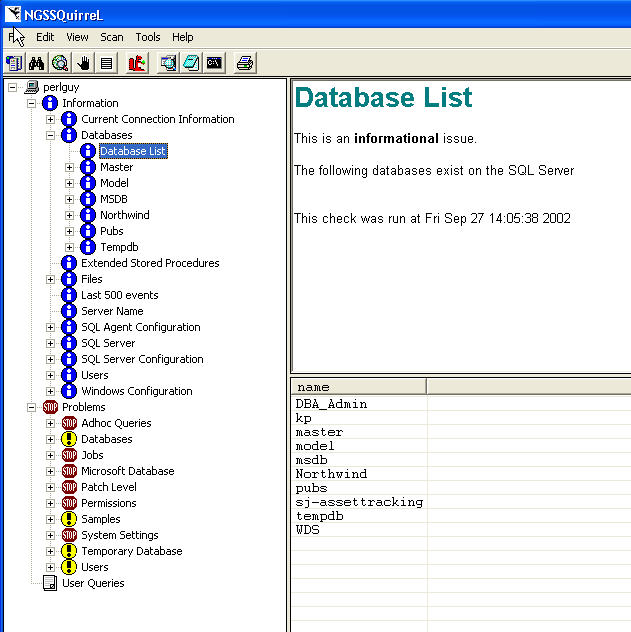
Each section works on a 3 pane model. The left tree is the section. The top right shows the name of the section and a brief description. The bottom left is a grid with the details. For example, if I select the "Databases" item and then the "Database List", I get an informational message in the upper right pane and then the details in the lower right pane. Most of the things in the informational section are nice to have to quickly check on the server. Some are a little cumbersome and would be nice to see them summarized. For example, if I select the "Server Roles" item under "Current Connection Information", then I see a list of the server roles. I would have to select each one to find out whether they apply to me. Not that I look at this information, but I wish it would be summarized with a single click.
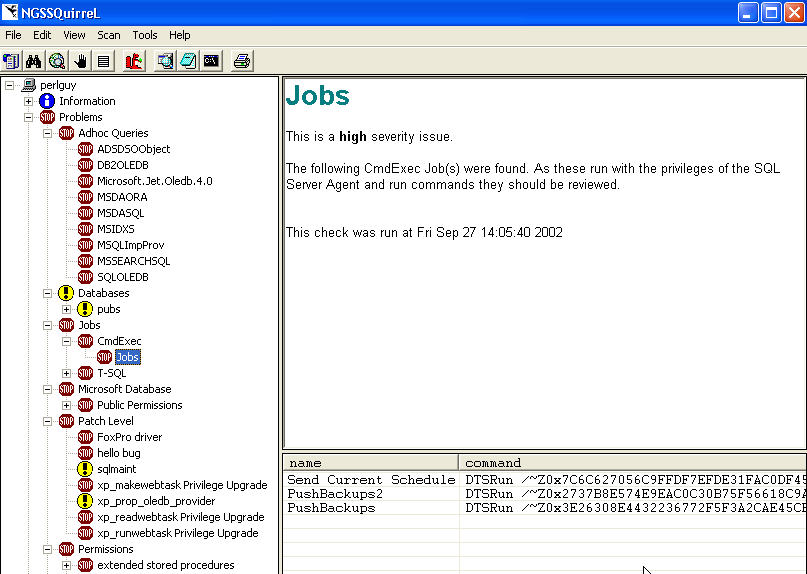
The problems folder is more interesting. It's broken down into a number of areas as shown in the diagram above. I've expanded them at the bottom of this review so you can see all of them. An icon next to each one informs you of high severity (stop sign) and medium (yellow question) issues. Selecting an item shows the problem and potential solutions. The bottom pane appears to show the result of some type of query or probe. I've selected a Stop Sign (high severity) item (the Jobs item) and shown the information and results that are shown.
The User Queries is an area where you can run queries, similar to query analyzer. I'm not sure how many people will use this functionality, or it's benefits since I have QA open pretty much all the time. However, it's basic functionality and it works, so I won't dwell on it.
One really neat thing is that you can right click an item and mark it for a fix. This allows you to specify exactly which items you want to mark. You can also mark (or unmark) at any level and it action will flow to all subitems.
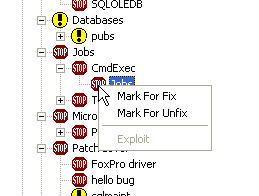
Then when you are ready, you can generate a lock down script that contains the commands needed for the fix. If this is applicable for an item, like the "allow other servers to connect over RPC", the script will contain the appropriate command (in this case sp_configure) to close this hole. I generated a lock down script by selecting "File | Generate Lock down Script". This occurs within a second and there is then a Lock down Script item appears under the left hand pane.
While I'm not sure which items I want to or need to control, this is extremely handy. Or for those times that I want to make a single change at a time. For items that have a patch, a hot link is included to the patch location (SP or HotFix). Another feature I really like is there is an "undo lock down" script also generated. This is something that is often overlooked by administrators of all types, but you should always have a backout script to remove your changes. I know it's a pain sometimes, but you can always build one and be sure you TEST it. I've included shots of the lockdown and undo scripts.
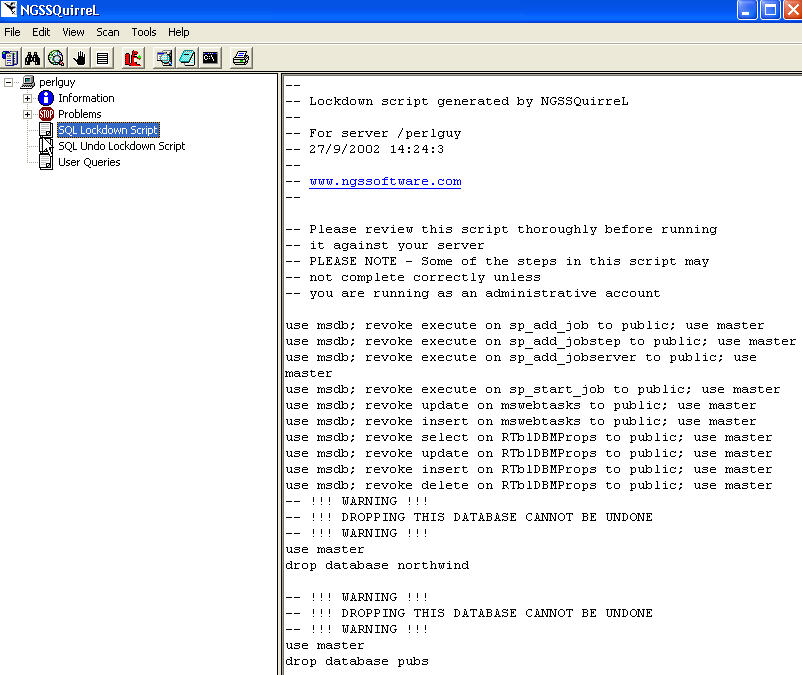
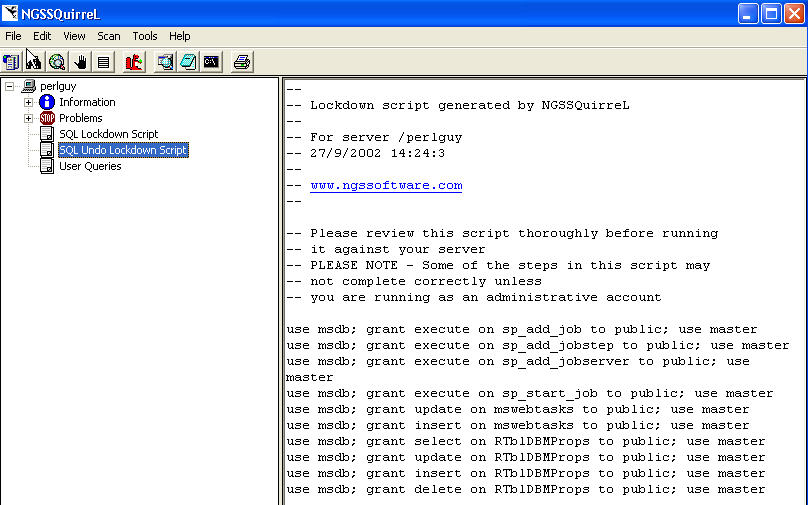
That's about it for a scan.
Other features.
You can print a report. Or export it to HTML, text, or Rich Text. You can save a scan as well. There are links to automatically launch a number of programs (notepad, command prompt, and Query Analyzer). Nice to have options. There is also an option for different connection types. 
There is a menu option for an Exploit Wizard, but selecting it told me that it wasn't available. I queried NGSSoftware and they had not decided whether or not this was worth including. For my 2 cents, it's not. Knowing the vulnerabilities is enough. I wouldn't run that type of utility against most of my servers anyway.
There are also options for specifying an instance name or using named pipes.
Impressions
I like this tool. It points out a number of vulnerabilities and does a better job than the Microsoft Security Baseline Analyzer (review) of finding vulnerabilities and showing them. It's a fairly polished tool and the GUI is straightforward and easy to understand. A number of items discovered by NGSSoftware are scanned in this tool, but alas, as of this writing, Microsoft has no patch for these items. The tool lets you know that.
It also lacks a few things, some of which I've emailed to NGS as possible enhancements. The ability to compare two scans, and see my patches taking effect would be nice. I'd also like the ability to "customize" the scans. One thing that I really didn't like about the MSBA and this tool is the fact that certain items are marked as security vulnerabilities, but they are not in my company. In the MSBA, having more than two system admins generates a flag. We always have at least 3, so I wish I could "turn this off" to remove the flag. In this tool I get high severity for DTS jobs that use DTSRun. It's nice to be aware this is an issue, but I have so many that having them show up as red flags is annoying.
I though the named instance config item should be included in the "Add Hosts" area and some of the wording in the informational panes could be improved (IMHO), but overall this is a well polished tool for a 1.0 piece of software. The updates are downloaded by the user after receiving an email from NGS. I couldn't test this because I haven't received any updates, but this is one area that MSBA is better by querying a database for updates. I suggested auto updates as well to NGSSoftware.
Conclusions
Is this tool worth buying? That's the bottom line for most of us. Given a price of ~$600 for a server, it's worth it for standardizing your patches and checking a server. In my environment, with dozens of SQL Servers, I'm not sure of the value of licensing for every server. Since we tend to do something to one server and later roll it out to all other servers, I'd probably use this on one server (my guinea pig) and perform the scanning and patching. Then I'd take these patches and apply them to the rest of the servers.
I'd give this product a 4 of 5 star rating. It works quickly and smoothly and provides a wealth of information. While it could use some polishing, it does the job well. The next version (according to NGSSoftware will also allow you to install the patches through the tool. Now that will be welcome! Also NGSSoftware loves feedback and is asking for suggestions and comments.
The bottom line, however, is that you should be patching your servers and you need a tool to do this. Either do the work manually or use a tool like this one. I think this tool works better than the MSBA, but it also comes at a price. It is definitely worth evaluating and I urge you to give it a try.
As always I welcome feedback on this article using the "Your Opinion" button below. Please also
rate this article.
Steve Jones
©dkRanch.net September 2002
In a nutshell

Vendor Information
Next Generation Security Software Limited
Surrey House
52 Throwley Way
Sutton
Surrey
SM1 4BF
United Kingdom
Phone:
email: ngssquirrel@ngssoftware.com
Website : http://www.ngssoftware.com
Pricing
NGSSquirrel
Price : UK 495 pounds / Server (includes a year of updates)
Contact NGSSoftware for multiple server pricing.
30 day full demos are available of all NGSSoftware Products
Problems Area: