The Politics of SQL Security
Dealing with SQL Server security when the application it uses is full of security holes.
Dealing with SQL Server security when the application it uses is full of security holes.
Glen Berry talks through a number of useful new developments in hardware, storage, and the Microsoft Windows and SQL Server ecosystem.
What are natively compiled stored procedures? Why would we want to use them and what are the performance benefits of using them over classic disk-based stored procedures?
This week Steve Jones looks at the formal way in which you might verify changes to your system. Do you have a process?
Denzil Ribeiro looks at the validation phase of transaction lifetime.
A brief comparison of three different JDBC Drivers built for connecting with MySQL
Branching code creates complexity to development and should be undertaken with caution.
What are your options for connecting to an Azure VM? Sure, a Remote Desktop Protocol (RDP) connection will get you started but you'll soon need a full secure VPN connection. Azure can provide three different options for doing this: Point-to-Site (P2S), Site-to-Site (S2S), and ExpressRoute, but what are their relative advantages, and which one is right for the way you need to use Azure?
This level starts with an overview of how versioning works in Git, a DVCS, and suggests a sensible database project versioning strategy. It then offers some simple, but illustrative, practical examples showing how to share database changes and deal gracefully with any conflicting changes.
By Steve Jones
AI is a big deal in 2026, and at Redgate, we’re experimenting with how...
By Steve Jones
Another of our values: The facing page has this quote: “We admire people who...
By Ed Elliott
Running tSQLt unit tests is great from Visual Studio but my development workflow...
Hi, We have low latency high volume system. I have a table having 3...
Comments posted to this topic are about the item The Long Name
Comments posted to this topic are about the item Eight Minutes
I run this code to create a table: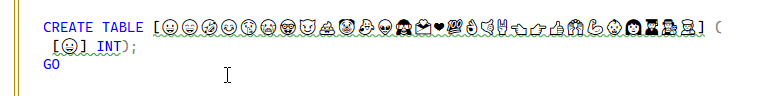 When I check the length, I get these results:
When I check the length, I get these results: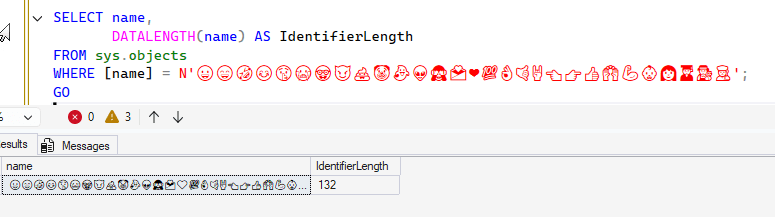 A table name is limited to 128 characters. How does this work?
A table name is limited to 128 characters. How does this work?