Security Shaming
This week Steve Jones looks at a new idea, rating the security of products publicly to try and shame vendors into more secure coding.
This week Steve Jones looks at a new idea, rating the security of products publicly to try and shame vendors into more secure coding.
Too many failovers can cause problems, as can those that happen to often. Steve Jones says you need to consider whether you always need to failover in a sitaution.
This article compares SELECT INTO and INSERT INTO under different scenarios, and the best approach preferred.
So often, the unexpected delays in delivering database code are more likely to happen after the developers initiate the release process. The necessary checks and tests can turn up surprises: The handover process can expose deficiencies. With good teamwork, planning and forethought, though, the process can be made almost painless.
As database developers, we may need to rethink the way we store and handle personal names
In this latest T-SQL Tuesday, Rob Farley takes a look at a couple of unexpected aspects of query plans you might observe when using Temporal Tables in SQL Server 2016.
Daniel Calbimonte walks through the steps to creating a SQL Server Reporting Services (SSRS) Report from an Analysis Services Tabular Database.
A how-to guide for configuring replication agents after a password change
By Steve Jones
AI is a big deal in 2026, and at Redgate, we’re experimenting with how...
By Steve Jones
Another of our values: The facing page has this quote: “We admire people who...
By Ed Elliott
Running tSQLt unit tests is great from Visual Studio but my development workflow...
Comments posted to this topic are about the item No Defaults Passwords Ever
Hi, We have low latency high volume system. I have a table having 3...
Comments posted to this topic are about the item The Long Name
I run this code to create a table: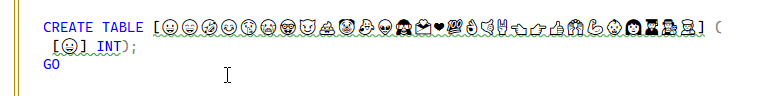 When I check the length, I get these results:
When I check the length, I get these results: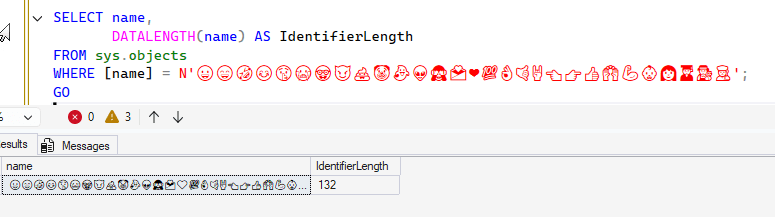 A table name is limited to 128 characters. How does this work?
A table name is limited to 128 characters. How does this work?