DB Security Workshop @ Oracle Montreal
I have
dedicated several posts on the importance of being a Data Steward, and the
consequences of not doing so, or in my
case having been prevented
from doing so within the government due to my ethnicity. But I digress… back to stressing
the significance of recurrent security training.
Last week, a colleague and I participated in an extremely interesting one-day workshop
at Oracle’s offices here in Montreal focused on information protection, privacy
and accountability. Here are some of the
notes I jotted down (full slides here) please excuse their terseness in advance:
It should be of no surprise, that a Verizon study report on data breaches reveals
that 70% are from internal users. There
are several strategies below you can use, and, by the way, if you did not catch
K. Brian Kelley’s Bulletproof
Security Strategy Webcast, it is worth the time.
Data breach legislation examples: CA Senate Bill 1386 Security Breach
Notification
Up and coming Bill C-12 Canadian data protection will make data
breach notifications mandatory (everyone say YAY!)
Beware of Malware
and hacking, since DBs are the top of the list for data breaches, because as we
database admin.s already know, 92% of the corporate data
is located there.
Breaches disclosure laws can cost companies $240/record (burnt, and ruins some
companies)
IOUG data security report says that 44% of users could access
data directly
48% not aware of all DBs with sensitive data
Obviously, the DBA working on these institutions did
not have a chance
to implement Database
Security Best Practices for the Vigilant DBA J
Compliance
and regulations are greater than ever - BASEL is the new acronym we heard also.
Fragmented response is typical and it is an afterthought to fix security – but as
I have said before, Databases are not a place to be lax on Security!
Solutions:
consolidate, automate and embed!
Oracle Security Inside Out, encryption, masking, multi-factor
authorization, secure configuration
Auditing and monitoring, blocking and logging, Access control (proper access
management)
HSM Hardware Security Device
Big picture is that there should be a DB firewall, another additional security
layer
– network SQL monitoring activity (to prevent unauthorized db
access), stop SQL injections, privilege or role escalation, and blocking.
Encrypted backups, encrypted Bus, encrypted exports, and data masking.
Highly accurate sql grammar based analysis.
DB data can
be sensitive, confidential or public:
audited with unauthorized local activity, consolidated DB security
TDE: Transparent DB encryption does not require
application changes; there is an Oracle security wallet
built-in key management, RMAN encrypt backups to disk, and encrypt export files
from Data pump
Master key has to be safeguarded because it controls all (chose the role of who should be our Master Key holder – delegate to the
responsible within a the security team, if available).
If you lose the Master key, you are SCREWED! L
All table space can be encrypted since it is highly efficient
Only REAL DBAs can open the Oracle Wallet (oops, sorry, that is an inside joke).
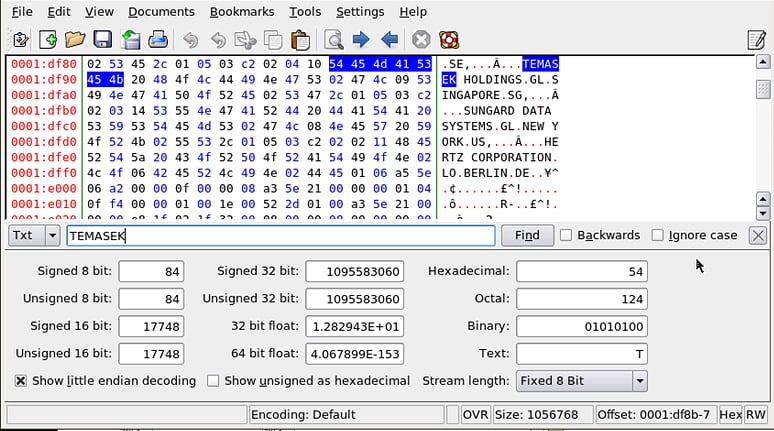
During our
Oracle encryption lab, we came across a tool to validate whether the data was
actually encrypted in the file (perhaps a file you can use too with SQL Server
encryption validation?).
Khexedit
allows us to view individual records from DBFs (data base files). We can see
the data unless TDE is enabled, since the TXT interprets the Hexi data value.
So after
altering the column to encrypt it, we can no longer find the data:
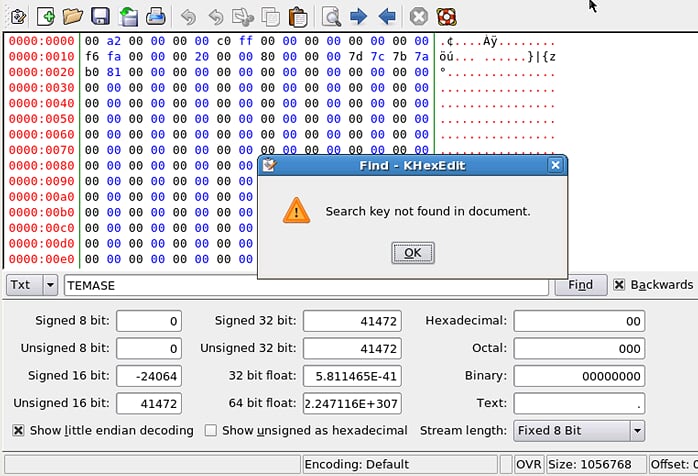
If you lose your keys – well, just do not lose them (or at least upon
generation, give them to the security team or your Boss/Manager, etc. to be
sure they are safe).
For more details here is a great FAQ
on Oracle Transparent Data Encryption (you can be I am going to read
up on SQL Server’s implementation of TDE next )
During the workshop we also covered Network encryption + strong authentication.
Standard based encryption for data in transit, strong authentication of users
and servers, no infrastructure changes required, easy to implement
Secure Backup product. Integrated
Tape or Cloud BU management
Masking removes the sensitive data from non-prod dbs –
a good practice for refreshes to all other environments outside of production!
Irreversible de-identification, while keeping referential integrity so apps
continue to work
Sensitive data never leaves the DB
DB Vault handles Separation of duties and
privileged user controls (let DBAs work with HR data without compromising
sensitive info).
Out of the box compliance reports,
centralized audit policy management.
Limits powers of privileged users by restricting highly privileged users to certain
operations,
Securely consolidate application data
No application changes required.
Consolidate audit data into secure repository
private DBs are were the vault will be used – access restriction features make
Oracle the lead
DB factor to secure, by IP, by account, by
realm violation audit reports can be built-in
Reports such as who is really in the DBA role
Prevent DBA from accessing application data, pre-build policies include realms
and command rules, complements application security, transparent to existing
applications, customizable.
Label security – classifying users
Total Recall – secure change
tracking
transparently track data changes
Efficient, tamper-resistant storage of archives,
real-time access to historical data,
simplified forensics and error correction
Data explosion depends on each application – those that are well developed will
auto-aggregate the data to save rows (as VM VCenter
databases do rather nicely).
Oracle Configuration management is much like grid control (aka enterprise
manager)
Continuous scanning against 375+ best practices and industry standards,
extensible
Detect and prevent unauthorized configuration changes
change management compliance reports...
A matter of taking the time to implement recommendations.
Rule of thumb: When in doubt, encrypt
encryption is a defacto expectation to protect data
PCI says any traces of Credit Card data have to be encrypted
encrypt personal identity info to comply with EU Data privacy
Medical records in DB might need to comply with CAAB 1298
Off-site backups should be encrypted.
Advanced security over the network…and
then we dove into the labs.
End of notes and warning - Failing
to be vigilant with data could also result in the loss of billions of dollars of
public money, a situation I unfortunately witnessed first-hand six months after
I had internally provided a report detailing an audit failure at Canada’s
largest public Institutionalized pension fund manager, the Quebec Deposit and Investment Fund (CDP Capital).
PS – if anyone is interested in Oracle Enterprise Manager 12c, here’s a great
webcast:


