Security is one of the most discussed topics for any cloud deployment plans and no organisation would like to compromise on security when they make that ‘final’ decision to move their database to the cloud.
In this blog post we will review how protected are our SQLDatabases within Windows Azure using firewalls.
I encountered couple of firewall related issues when I first started working with Windows Azure, and that motivated me to write this blog post.
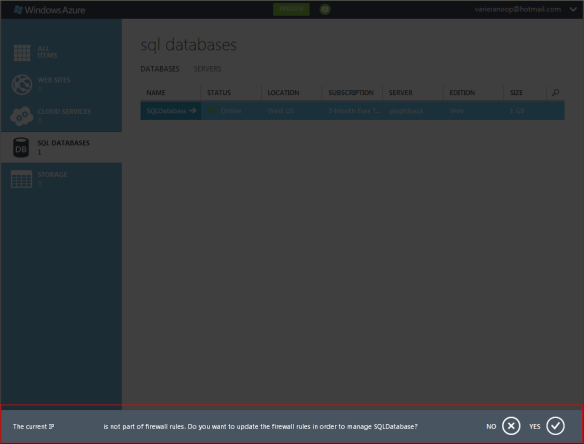
One of the error message or a warning was
The error message was pretty much saying that the IP address (Hidden in the picture) is not configured to manage the SQLDatabase within the server.
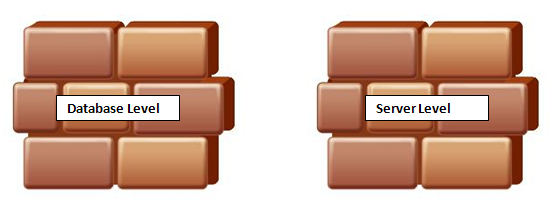
Before we see how we can configure the IP address to grant access, we will need to review what levels of firewall rules can be set on Windows Azure.
We can set firewall rules at Server Level and Database Level
Server level rule simply means that a client within a particular IP or within a range can access all your databases within the same SQLDatabase server.
In case you would like to restrict a client with a specific IP or a range of IPs to access only specific databases within the SQLDatabase server, then the role of Database Level firewall rules pitch in.
SQLDatabase firewall is considered very important within Windows Azure architecture. Connection attempts from the Internet and Windows Azure must first pass through the SQL Database firewall before they can reach your SQL Database server or database.
Let’s consider a simple example to learn this in a better way -
When computer A tries to connect SQLDatabase Server from web, then the originating IP address is first checked by the SQLDatabase firewall against the server level firewall and grants access if the IP is within server level range. It will check the database level firewall rule in case the IP is not found within server level firewall range and connection is granted for the specific database in case the IP falls in database level rule.
Setting up server level rules
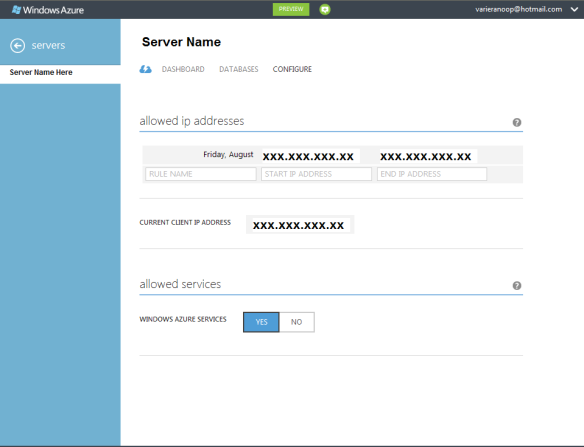
The easiest method to create a Server level firewall is via the Windows Azure portal itself.
We will need to select the server and choose the Config option to set a range of IPs or a single IP.
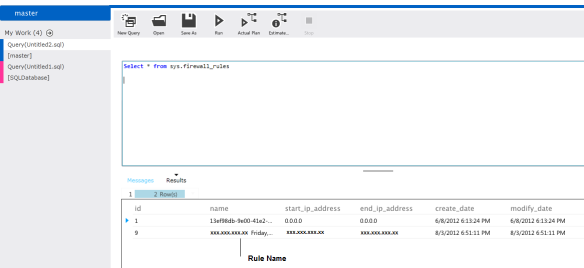
We have the option to check what all IPs or IP ranges are configured at server level using view sys.firewall_rules after connecting to master database.
Setting up database level rules
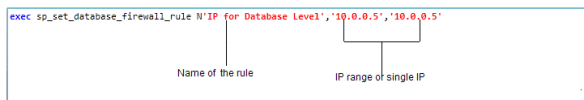
The recommended approach to create a database level firewall is to use the stored procedure sp_set_database_firewall_rule
We will need to connect to the exact database for which we need to create the rule and run the stored procedure with the parameters.
[The IP mentioned above is just a test case one]
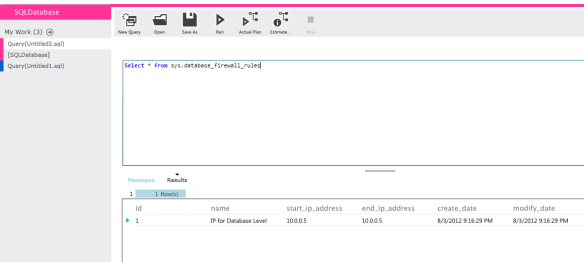
The database level IPs or range can be checked using another view sys.database_firewall_rules and we will need to connect to the database and run this view to get the accurate details.
A request with IP 10.0.0.5 will be able to access only the database for which the rule was set and not all the databases within the SQLDatabase server.
Conclusion
There is good amount of protection available on Windows Azure platform for protecting your mission critical SQLDatabases and in this post we had a quick overview of firewall level protection.
You can read more about the comprehensive security concepts for a SQLDatabase on Windows Azure here -
Windows Azure SQL Database Connection Security
Keep checking this space for more and there are lots of new and exciting stuff coming up !
This post is in continuation with my earlier posts
SQLSailor is exploring(Part1) – Creating my first SQL Database on Windows Azure
SQLSailor is exploring(Part 2) – Managing SQL Databases on Windows Azure
SQLSailor is exploring(Part3) – Designing SQL Databases on Windows Azure
SQLSailor is exploring(Part4) – Basic DML,DDL operations with SQL Databases on Windows Azure
SQLSailor is exploring(Part5) – SQLDatabase Dashboard on Windows Azure
Thanks for reading.