SQL Server is a relational database management product developed by Microsoft. It is prominently deployed by enterprises all over the world to securely maintain crucial database in a well-organized manner. As we all know, nowadays, the digital crimes constantly increases and someone insider or outsider involve in it. In fact, in SQL Server, some terminated employees or external hacker intentionally changes the sensitive database values before leaving the organization to affect the assets of it.
But, there is a good news!
However, some advanced SQL tools and functions are available through which we can perform forensic analysis on updated values of database tables. By this, Organizations can find out that at what time the values were changed. So, go through the article once when you really care about your sensitive SQL Server database.
A Handy Solution for Forensic Analysis on Updated Values of Database Tables
The transaction log file is needed to examine which SQL Server database table was updated or changed. The T-log saved all the transaction along with timestamp that occurs in database. So, T-log file is the way through which Organizations can do forensic analysis on updated values of database tables. However, the data stored in transaction log file is not in a human-readable format. So, in order to access its content for forensic purposes, a function is provided by Microsoft SQL Server Database i.e., fn_dblog(). It is an undocumented function whose works is to read the T-log information and shows on the console in a readable format. Now, check out how to use fn_dblog() to verify the updated operation.
Step 1: Update the SQL Server Database Table
Here, we take an example where we have already created a table whose name is Employee. Also, we update a value in the table by using the following instructions.
Step-1: Use ‘Select’ command to view the content of table as shown in the screenshot.
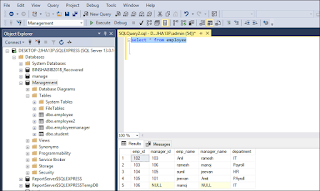
Now, we are going to change the department of an employee whose emp_id is 104. To do this, use Update employee set department = ‘IT’ where emp_name = ‘Jeevan’.
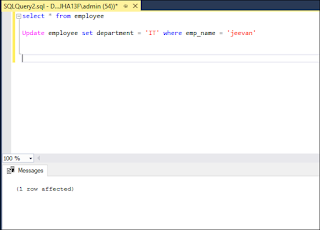
Step 2: Check Whether Table Gets Updated
After completing the first step, again execute ‘Select * from employee’ command to verify whether the department gets modified or not.

Step 3: Use fn_dblog() to Get Information About Update Operation
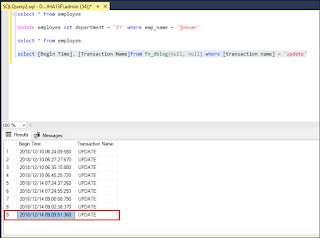
It is an interesting part where an Organization can find out that someone intentionally changes the values in database without permission with the help of fn_dblog(). User needs to run the following command to get the detail about last update operation happens in database.
Select [Begin Time], [Transaction Name] from fn_dblog(null, null) where [Transaction Name] = ‘update’

Unfortunately, Fn_dblog() Has Some Limitations
Everything has its own pros and cons. Same situation well expresses for fn_dblog() function. It is available as free of cost and shows various information from the T-log file. However, it only shows that updated operation applied on database but not the data which gets updated. So, a user cannot get exact information about the database table. So, it is advised to use the second technique for forensic analysis on updated values of database tables.
Impeccable SQL Log Analyzer for Extensively Analyses T-Log File
SysTools SQL Log Viewer is an automated utility that deeply scans transaction log file of SQL Server database. It provides complete data of a database like Login Name, Time, Table Name, Transaction Name, and Query in a readable format. Also, this tool can support Transaction log (or LDF) files of SQL Server 2017, 2016, 2014, 2012, 2008, and SQL Server 2005. Apart from this, the tool has various features that make it ideal for forensic analysis on updated values of database tables.
1. In-Depth Examination of T-Log File
With the help of this tool, one can preview the complete data of T-log file along with SQL query. The best part is user can restore the last data table on which updated command executed back into the SQL Server. For this, one has to select the database from left side navigation panel. After that, select any row from the preview pane and gets its data on the software panel. Hence, it performs forensic analysis as well as recovers the modified table data.
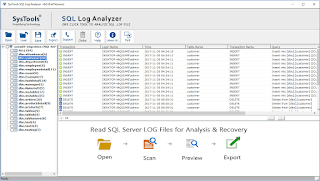
2. Get Back the Updated Data
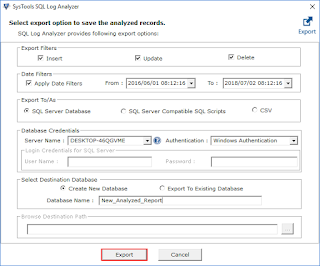
The software provides an option to export the record that was updated back into the SQL Server. A user can transfer the data directly into SQL Server Database, SQL Server Compatible Scripts, or CSV. In fact, they can save exported data either into the Existing database or New database. Along with this, the two different filters are also provided.
- Export Filters: This feature is used to select the transaction operation such as Insert, Update, or Delete. One can choose any of the options. So, the tool can export only that transaction data in the database.
- Date Filters: With the help of this characteristic, the users can restore data of a specified timeline.
What Say, Does Above Methods Accurately Analyze Updated Values of Database Tables?
The objective of this write-up is to provide complete knowledge about forensic analysis on updated values of database tables. Because if anyone changes the database with the wrong intention, then it is must to identify what data get disturbed in order to prevent the business data loss. Therefore, we have discussed SQL Server fn_dblog() function, but it is not an ideal way to retrieve information from T-log file. So, we have also discussed an ultrafast SQL Log Analyzer tool to overcome all the limitations of manual procedure.