More than 115,000 websites—many run by major universities, government organizations, and media companies—remained wide open to hacker takeovers because they hadn’t installed critical patches released 10 weeks ago, security researcher Troy Mursch said Monday. A separate researcher reported on Tuesday that many of the sites were already compromised and were being used to surreptitiously mine cryptocurrencies or push malware on unsuspecting visitors.
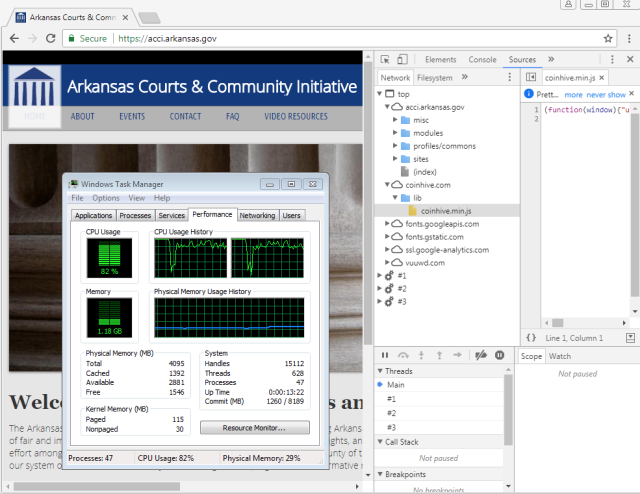
Infected pages included those belonging to the University of Southern California, Computer World’s Brazil site, and the Arkansas Judiciary’s Courts and Community Initiative, which were causing visitors’ computers to run resource-intensive code that mines cryptocurrency, Jérôme Segura, lead malware intelligence analyst at antivirus provider Malwarebytes, told Ars.
Segura said a Harvard University page that earlier was also infected with mining malware had since been defaced, presumably by a different party. Meanwhile, a Western Michigan University page that earlier was infected with code that pushed a malicious browser extension was later repaired. Segura reported his findings Tuesday and has indexed more than 900 infected sites here.
The lack of patching and the site takeovers that it makes possible come after Drupal maintainers released an update in March that allowed hackers to remotely execute code of their choice. The severity of the vulnerability patched, combined with the ease in exploiting it, quickly earned the flaw the nickname Drupalgeddon2, a throwback to a similar 2014 Drupal vulnerability that came under mass exploit within hours of a patch being released. Drupal maintainers patched a separate code-execution vulnerability in April. In the weeks following the March and April vulnerability disclosures came independently released proof-of-concept exploits that provided a blueprint for malicious hackers to use. Almost immediately after the release of the April patch, the underlying vulnerability came under attack, but it so far has proven harder to successfully exploit.
Despite the real-world threat of exploitation, more than 115,000 websites as of Monday continued to run outdated versions of content management systems that are vulnerable to Drupalgeddon2, Mursch reported. The researcher said it wasn’t clear what version of Drupal another 225,000 sites he scanned were using, leaving open the possibility that some of them may also be vulnerable to takeover. Slightly more than 134,000 sites running Drupal showed they were running versions that weren't vulnerable. It's possible some of the outdated sites are running mitigations that prevent Drupalgeddon2 exploits from working, but the mass exploits reported by Malwarebytes suggest that many are not.
Segura said many of the infected sites are pushing code that causes visitors’ computers to surreptitiously mine cryptocurrencies on behalf of the attackers. In other cases, the attackers cause the Web servers themselves to carry out the compute-intensive mining. Still other attacks are causing the vulnerable websites to push tech support scams or malicious wares.
The most up-to-date versions of Drupal are 7.59 and 8.5.4. Update: About 14 hours after this post went live, Drupal maintainers provided a statement that said they disagreed with the methodology Mursch used to determine if sites were vulnerable to Drupalgeddon2. The statement reads in part:
Those reports are all based on the same source. The source investigated the contents of CHANGELOG.txt of a large number of sites and assumed all sites reporting a version lower than 7.58 to be vulnerable.
Checking the contents of CHANGELOG.txt is not a valid way to determine whether a site is vulnerable to any given attack vector. Patches distributed by the Drupal security team to fix the issues were widely used, but did not touch CHANGELOG.txt or any version strings defined elsewhere. There are also other mitigations that vendors have provided which would also not affect CHANGELOG.txt but would protect the site.
We believe the presented numbers to be inaccurate. We consider it to be misleading to draw conclusions from this sparse information. The Drupal project has a long history of a reliable coordinated disclosure security program. For the past 4 years, the Drupal Security Team has provided support to journalists covering our releases and policies and is available for further enquiries.
reader comments
44