
For almost two years, Ars has advised readers to use a software-based password manager to ease the password fatigue that comes from choosing and securing dozens of hard-to-guess passcodes that are unique to each site or service. A research paper scheduled to be presented at a security conference next month underscores the hidden dangers of selecting the wrong products.
The researchers examined LastPass and four other Web-based managers and found critical defects in all of them. The worst of the bugs allowed an attacker to remotely siphon plaintext passcodes out of users' wallets with no outward sign that anything was amiss. LastPass and three of the four other developers have since fixed the flaws, but the findings should serve as a wakeup call. If academic researchers from the University of California at Berkeley can devise these sorts of crippling attacks, so too can crooks who regularly case people's online bank accounts and other digital assets.
"Widespread adoption of insecure password managers could make things worse: adding a new, untested single point of failure to the Web authentication ecosystem," the researchers wrote in their paper, titled The Emperor's New Password Manager: Security Analysis of Web-based Password Managers (PDF). "After all, a vulnerability in a password manager could allow an attacker to steal all passwords for a user in a single swoop. Given the increasing popularity of password managers, the possibility of vulnerable password managers is disconcerting and motivates our work."The most serious of the defects was uncovered in LastPass, a manager that had at least one million users as of 2011. A bug in a "bookmarklet" feature used to automatically enter passwords into websites made it possible for malicious code planted on one site to steal credentials for other sites. An attacker might exploit the vulnerability by compromising a site a user was using LastPass to access. As soon as the user clicked on the bookmarklet, the attacker could surreptitiously steal plaintext passwords belonging to other sites that were also secured by LastPass.
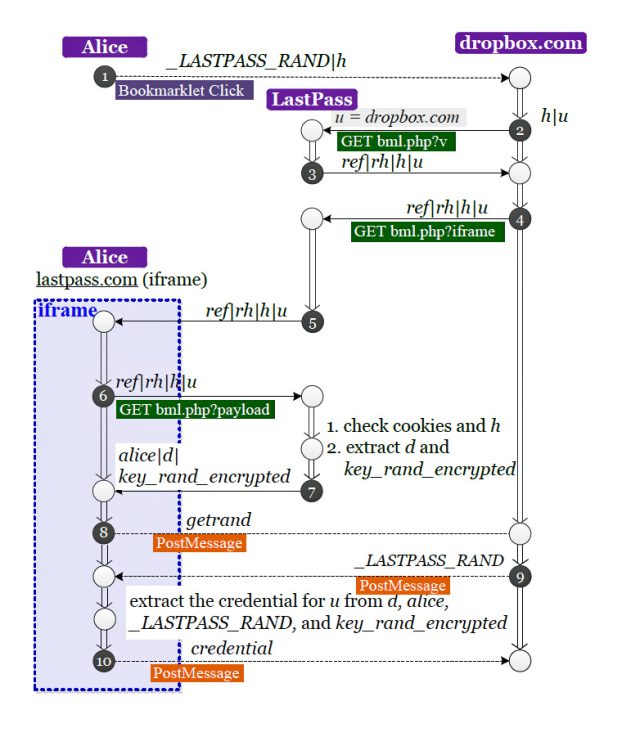
marklet.
A second flaw in LastPass made it possible for malicious code on a website to extract the encrypted password database and other sensitive information belonging to users whose e-mail address is known to the attacker. The adversaries could then wage an offline cracking attack against the database in hopes of decrypting it. Attackers could also exploit the bug to discover other sites a person was using LastPass with. LastPass officials published a blog post Friday that describes the bugs and reports that there are no indications that they have ever been actively exploited.
Other Web-based password managers analyzed in the study performed no better. A flaw in PasswordBox, for instance, made it possible for attackers to steal millions of users' full names, usernames, and the URLs where passwords were entered. The researchers also uncovered serious flaws in RoboForm, My1login, and NeedMyPassword. With the exception of NeedMyPassword, the other providers promptly responded to researchers' private notifications with fixes that address all serious defects discovered in the research. NeedMyPassword has yet to reply at all, the researchers said.
All five of the providers develop Web-based managers. By storing passwords in the cloud or otherwise interacting with online apps when storing or managing large numbers of passcodes, the managers provide functionality not available to users of an application running on a single computer. For instance, passwords can be easily shared among a user's smartphone and home and office computers. But the cloud-based capabilities also opened up holes that attackers could exploit. The researchers didn't study non Web-based managers, so it doesn't automatically follow that they are more secure. In their paper, the researchers wrote:
Our attacks are severe: in four out of the five password managers we studied, an attacker can learn a user’s credentials for arbitrary websites. We find vulnerabilities in diverse features like one-time passwords, bookmarklets, and shared passwords. The root-causes of the vulnerabilities are also diverse: ranging from logic and authorization mistakes to misunderstandings about the web security model, in addition to vulnerabilities like CSRF and XSS.
On the whole, readers are likely better off using a password manager than they are using the same password for multiple sites. For that reason, Ars still recommends that people use a password manager. However, readers should remember that password managers represent a single point of failure that could lead to the complete compromise of virtually every website account they have. It's not possible to know which managers are safer than others without a trusted third-party conducting a detailed assessment on each one. That said, well-known managers that have been available for years are probably more trustworthy than a newer one that was recently introduced into the market.
Besides demonstrating how easy it is to spot serious flaws, the paper presented guidelines to prevent or mitigate future flaws. Password manager developers would do well to closely study the paper and thoroughly analyze whether any of the code they're responsible for suffers from any of the same mistakes. Providers that truly value security should hire outside security auditors to fully test the managers against a fully battery of real-world tests. Given the growing popularity of password managers, the failure to properly secure them could be dire.
"Millions of users trust these vulnerable password managers to securely store their secrets," the researchers wrote. Our study strikes a notion of caution: while in theory password managers provide a number of advantages, it appears that real-world password managers are often insecure."

reader comments
188